Data Fabric Security on AWS
Partner Solution Deployment Guide

May 2023
Jenifer Wang, Solution Acceleration team (DoD)
Troy Ameigh, AWS Partner Intergration and Engineering team

| Refer to the GitHub repository to view source files, report bugs, submit feature ideas, and post feedback about this Partner Solution. To comment on the documentation, refer to Feedback. |
This Partner Solution was created by Immuta and Radiant Logic in collaboration with Amazon Web Services (AWS). Partner Solutions are automated reference deployments that help people deploy popular technologies on AWS according to AWS best practices. If you’re unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Overview
This guide covers the information you need to deploy the Data Fabric Security Partner Solution in the AWS Cloud.
Costs and licenses
This deployment requires licenses for Immuta and RadiantOne. For more information, refer to the Immuta and Radiant Logic websites, respectively. There is no cost to use this Partner Solution, but you will be billed for any AWS services or resources that this Partner Solution deploys. For more information, refer to the AWS Partner Solution General Information Guide.
Architecture
Deploying this Partner Solution with default parameters builds the following Data Fabric Security environment in the AWS Cloud.
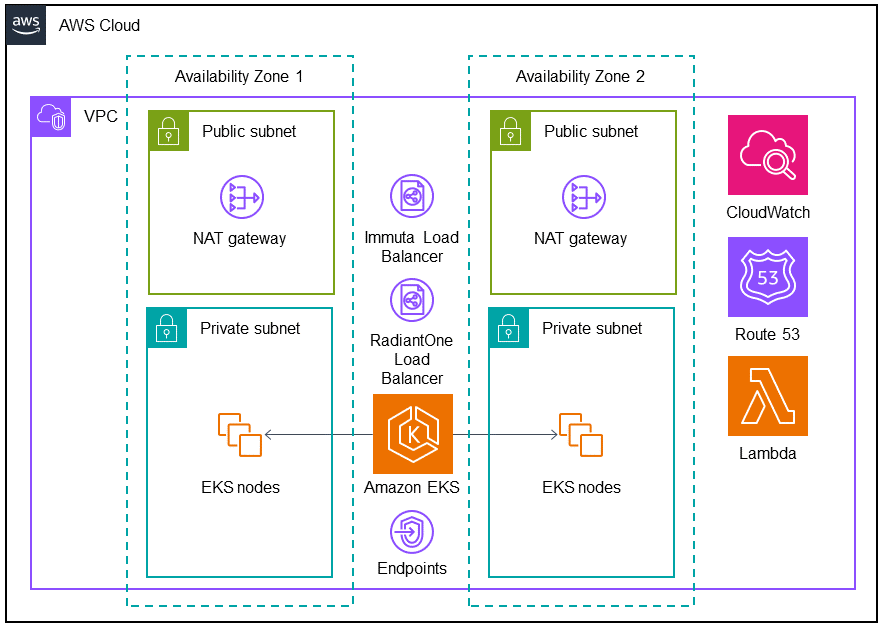
As shown in Figure 1, this Partner Solution sets up the following:
-
An architecture that spans two Availability Zones.*
-
A virtual private cloud (VPC) configured with public and private subnets, according to AWS best practices, to provide you with your own virtual network on AWS.*
-
In the public subnets, NAT gateways to allow outbound internet access for resources in the private subnets.*
-
Two Classic Load Balancers, one each for the Immuta and RadiantOne services in the private subnets.
-
In the private subnets:
-
Three-node Amazon EKS clusters containing highly-available deployments of Immuta and RadiantOne.
-
Amazon EKS to provide the Kubernetes control plane for the clusters.
-
Endpoints for other AWS services to access the Amazon EKS Kubernetes API server.
-
-
Amazon CloudWatch to collect, store, access, and monitor logs.
-
Amazon Route 53 for a private hosted zone and resolvers.
-
AWS Lambda to install Immuta and RadiantOne.
* You can choose to use an existing VPC during deployment. The existing VPC must include two private subnets in separate Availability Zones.
Predeployment steps
-
Install Node.js 18.0.0 or later. For more information, refer to Tutorial: Setting Up Node.js on an Amazon EC2 Instance.
-
Install AWS Cloud Development Kit (AWS CDK) using Node Package Manager (npm).
npm install -g aws-cdkFor more information, refer to Getting started with the AWS CDK.
-
Load your AWS credentials into your development environment. You can do this with the AWS Command Line Interface (AWS CLI). For more information, refer to Authentication with AWS.
-
Obtain licenses for Immuta and RadiantOne. For more information, refer to the Immuta and Radiant Logic websites, respectively.
After purchasing an Immuta license, you will receive a user name and password from Immuta. Enter the Immuta user name and password for the Instance.UsernameandInstance.Passwordparameters indev.yamlwhen configuring for deployment.
Deployment steps
-
Navigate to the Data Fabric Security root folder.
cd <path>/quickstart-aws-data-fabric-security -
Install all packages.
npm ci -
Open the file
<path>/quickstart-aws-data-fabric-security/config/dev.yaml. -
Edit the variables to customize the deployment for your environment. For variable details, refer to Deployment configuration, later in this guide.
-
Run the following command to bootstrap your AWS environment.
cdk bootstrap aws://<ACCOUNT_ID>/<REGION> -
Deploy the solution.
bash dfs-solution-install.shThe solution takes about 20 minutes to deploy. -
Once deployment is complete, Copy the output from the deployment and save it for later use. The following is an example of output for
DataFabricStack.DataFabricStack.ExportsOutputFnGetAttdatafabricsecuritycorestackNestedStackdatafabricsecuritycorestackNestedStackResource0E29B9E3OutputsDataFabricStackdatafabricsecuritycorestackdatafabricsecurityhostedzone8A7A666ERef412EFD8E = Z08846025FQL5G34G3RSN DataFabricStack.ExportsOutputFnGetAttdatafabricsecuritycorestackNestedStackdatafabricsecuritycorestackNestedStackResource0E29B9E3OutputsDataFabricStackdatafabricsecuritycorestackdatafabricsecurityvpc3D851B3DRef8F8BED20 = vpc-0k86a8r6550x470sd DataFabricStack.ExportsOutputFnGetAttdatafabricsecuritycorestackNestedStackdatafabricsecuritycorestackNestedStackResource0E29B9E3OutputsDataFabricStackdatafabricsecuritycorestackdatafabricsecurityvpcPrivateSubnet1SubnetD144D644RefCA2E36A0 = subnet-05c58c03655b07e96 DataFabricStack.ExportsOutputFnGetAttdatafabricsecuritycorestackNestedStackdatafabricsecuritycorestackNestedStackResource0E29B9E3OutputsDataFabricStackdatafabricsecuritycorestackdatafabricsecurityvpcPrivateSubnet2SubnetC59876D4RefB9149745 = subnet-0355b2b6384b7a984 DataFabricStack.ExportsOutputFnGetAttdatafabricsecuritycorestackNestedStackdatafabricsecuritycorestackNestedStackResource0E29B9E3OutputsDataFabricStackdatafabricsecuritycorestackdatafabricsecurityvpcPublicSubnet1Subnet364D7A24RefCE325DB3 = subnet-0b384f6b1a3cdee0d DataFabricStack.ExportsOutputFnGetAttdatafabricsecuritycorestackNestedStackdatafabricsecuritycorestackNestedStackResource0E29B9E3OutputsDataFabricStackdatafabricsecuritycorestackdatafabricsecurityvpcPublicSubnet2SubnetE8E85537RefFE30536F = subnet-09eaf0abdec1vf6e2 DataFabricStack.ExportsOutputFnGetAttdatafabricsecuritykeyEF30DCE5Arn6660AD21 = arn:aws-us-gov:kms:us-gov-west-1:123456789012:key/a5n6bs39-8yfr-7tww-m544-57bk737tay0f DataFabricStack.ExportsOutputRefdatafabricsecuritykubectl66B18AE6595A4A51 = arn:aws-us-gov:lambda:us-gov-west-1:123456789012:layer:datafabricsecuritykubectl44B16AB6:5The following is an example of output for
DataFabricStack/data-fabric-security-eks-cluster.DataFabricStackdatafabricsecurityeksclusterCA551CED.ClusterArn = arn:aws-us-gov:eks:us-gov-west-1:123456789012:cluster/data-fabric-security-eks-cluster DataFabricStackdatafabricsecurityeksclusterCA551CED.EKSAdminRole = arn:aws-us-gov:iam::123456789012:role/DataFabricStackdatafabric-datafabricsecurityeksclu-16OBLBQDF1383 DataFabricStackdatafabricsecurityeksclusterCA551CED.datafabricsecurityadminplatformteamteamadmin = arn:aws-us-gov:iam::123456789012:role/Admin DataFabricStackdatafabricsecurityeksclusterCA551CED.datafabricsecurityeksclusterClusterName6BCF1F10 = data-fabric-security-eks-cluster DataFabricStackdatafabricsecurityeksclusterCA551CED.datafabricsecurityeksclusterConfigCommand978D3532 = aws eks update-kubeconfig --name data-fabric-security-eks-cluster --region us-gov-west-1 --role-arn arn:aws-us-gov:iam::123456789012:role/DataFabricStackdatafabric-datafabricsecurityeksclu-14T5IMKRMS7JT DataFabricStackdatafabricsecurityeksclusterCA551CED.datafabricsecurityeksclusterGetTokenCommand1D6ABA05 = aws eks get-token --cluster-name data-fabric-security-eks-cluster --region us-gov-west-1 --role-arn arn:aws-us-gov:iam::123456789012:role/DataFabricStackdatafabric-datafabricsecurityeksclu-14T5IMKRMS7JT
Deployment configuration
Edit the variables in config/dev.yaml to customize the deployment for your environment.
Global parameters
| Parameter | Description | Default |
|---|---|---|
AWSAccountID |
AWS account ID. |
|
AWSRegion |
AWS Region. |
|
Domain |
Domain name. |
|
Networking parameters
| Parameter | Description | Default |
|---|---|---|
VpcId |
Enter an existing VPC ID or leave blank ( |
|
SubnetA |
Private subnet in Availability Zone 1. To create a new subnet, delete default entry and leave blank ( |
|
SubnetB |
Private subnet in Availability Zone 2. To create a new subnet, delete default entry and leave blank ( |
|
MaxAZs |
Maximum number of Availability Zones. |
|
Amazon EKS parameters
| Parameter | Description | Default |
|---|---|---|
Clustername |
Custom name for the EKS cluster. |
|
EKSAdminRole |
Amazon Resource Name (ARN) of an existing IAM role in the AWS account with |
|
EKSEndpointAccess |
Amazon EKS endpoint access type ( |
|
InstanceType |
EKS cluster instance type. |
|
ClusterSize |
EKS cluster size. |
|
Immuta parameters
| Parameter | Description | Default |
|---|---|---|
Deploy |
Enter |
|
ChartVersion |
Immuta Helm Chart version. |
|
ImmutaVersion |
Version of Immuta to install. |
|
ImageTag |
Docker image tag. |
|
Instance.Username |
Immuta instance user name. |
|
Instance.Password |
Immuta instance password. |
|
Database.ImmutaDBPassword |
Immuta database password. |
|
Database.ImmutaDBSuperUserPassword |
Immuta database super user password. |
|
Database.ImmutaDBReplicationPassword |
Immuta database replication password. |
|
Database.ImmutaDBPatroniApiPassword |
Immuta database Patroni API password . |
|
Query.ImmutaQEPassword |
Query engine password. |
|
Query.ImmutaQESuperUserPassword |
Query engine super user password. |
|
Query.ImmutaQEReplicationPassword |
Query engine replication password. |
|
Query.ImmutaQEPatroniApiPassword |
Query engine Patroni API password. |
|
RadiantOne parameters
| Parameter | Description | Default |
|---|---|---|
Deploy |
Enter |
|
ZkImageTag |
Zookeeper image tag. |
|
FidImageTag |
FID image tag. |
|
License |
RadiantOne license. |
|
RootPassword |
Root administrator user password. |
|
Postdeployment steps
Sign in to RadiantOne
You must connect to RadiantOne from inside the environment (bastion host) or by configuring your local DNS to point the RadiantOne hostname to the RadiantOne load balancer.
-
Navigate to one of the following URLs.
-
http://radiantlogic.example.com:7070 -
https://radiantlogic.example.com:7171
-
-
On the RadiantOne main control panel, enter username
cn=directory manager. -
For the password, enter the value of the
RootPasswordparameter indev.yaml. Refer to Deployment configuration, earlier in this guide. -
Choose Login.
Sign in to Immuta
-
Connect to
https://immuta.<example.com>. Replace<example.com>with the domain name entered for theDomainparameter indev.yaml. Refer to Deployment configuration, earlier in this guide. -
Enter an email address and password to create a new administrator account.
-
On the License page, choose Add license key.
-
Enter the Immuta license provided by Immuta.
-
Choose Save.
Immuta AWS GovCloud region support
Immuta comes with support for standard AWS Regions. Complete the following steps to configure AWS GovCloud support in Immuta.
-
In Immuta, choose App Settings.
-
Choose Advanced Settings.
-
Choose Advanced Configuration.
-
Enter the following in the Advanced Configuration text box.
client: awsRegions: - us-gov-east-1 - us-gov-west-1 -
Choose Save
Uninstall the Partner Solution
To uninstall the Partner Solution, complete the following steps.
Step 1: Run the Lambda uninstall functions for Immuta and RadiantOne
-
Sign in to the AWS Management Console and open the AWS Lambda console.
-
On the Functions page, choose the data-fabric-security-immuta-uninstall function.
-
On the Code tab, choose Test.
-
On the Configure test event window, enter an event name.
-
Choose Save.
-
Choose the Test button to run the test.
-
Navigate to the Functions page.
-
Choose the data-fabric-security-radiantlogic-uninstall function.
-
Repeat steps 3–6.
Step 2: Uninstall the deployment stacks
To uninstall the deployment stacks, run the following command.
./dfs-solution-uninstall.shAdditional resources
RadiantOne
Troubleshooting
Radiant Logic license not working
When configuring the deployment, enter your RadiantOne license from Radiant Logic in the License parameter in dev.yaml. Ensure that you escape the curly braces when entering configuring the parameter; for example:
"\\{rlib\\}<RADIANT_LOGIC_LICENSE>"
For more information, refer to Deployment steps, earlier in this guide.
For troubleshooting common Partner Solution issues, refer to the AWS Partner Solution General Information Guide.
Customer responsibility
After you deploy a Partner Solution, confirm that your resources and services are updated and configured—including any required patches—to meet your security and other needs. For more information, refer to the Shared Responsibility Model.
Feedback
To submit feature ideas and report bugs, use the Issues section of the GitHub repository for this Partner Solution. To submit code, refer to the Partner Solution Contributor’s Guide. To submit feedback on this deployment guide, use the following GitHub links:
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS products or services, each of which is provided "as is" without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at https://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "as is" basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.