Amazon Aurora MySQL Database on AWS
Partner Solution Deployment Guide

March 2021
Arabinda Pani, AWS PSA Database Specialist team
Dave May, AWS Integration and Automation team

| Refer to the GitHub repository to view source files, report bugs, submit feature ideas, and post feedback about this Partner Solution. To comment on the documentation, refer to Feedback. |
This Partner Solution was created by Amazon Web Services (AWS). Partner Solutions are automated reference deployments that help people deploy popular technologies on AWS according to AWS best practices. If you’re unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Overview
This guide covers the information you need to deploy the Amazon Aurora MySQL Database Partner Solution in the AWS Cloud.
Amazon Aurora is a fully managed relational database engine that’s compatible with MySQL and PostgreSQL. With Aurora, you can use the code, tools, and applications you use today with your existing MySQL and PostgreSQL databases. For some workloads, Aurora can deliver up to five times the throughput of MySQL without requiring changes to most of your existing applications.
As part of Amazon Relational Database Service (Amazon RDS), Aurora takes advantage of Amazon RDS features for database management and administration. It eliminates the need to maintain database infrastructure: servers, replication, backups, and so on.
This Amazon Web Services (AWS) Partner Solution deploys [<product name>](<partner’s marketing product page>) in the AWS Cloud so that <purpose>. This solution is for users who are looking for a repeatable, customizable reference architecture for Aurora MySQL using AWS CloudFormation.
You can also use this Partner Solution as a building block for other automated deployments. To do this, use the existing-VPC deployment option, which creates only the Aurora database components. The template for this option plugs in to your existing AWS CloudFormation templates and replaces your MySQL database.
Costs and licenses
There is no cost to use this Partner Solution, but you will be billed for any AWS services or resources that this Partner Solution deploys. For more information, refer to the AWS Partner Solution General Information Guide.
Architecture
Deploying this Partner Solution with default parameters builds the following Aurora MySQL environment in the AWS Cloud.
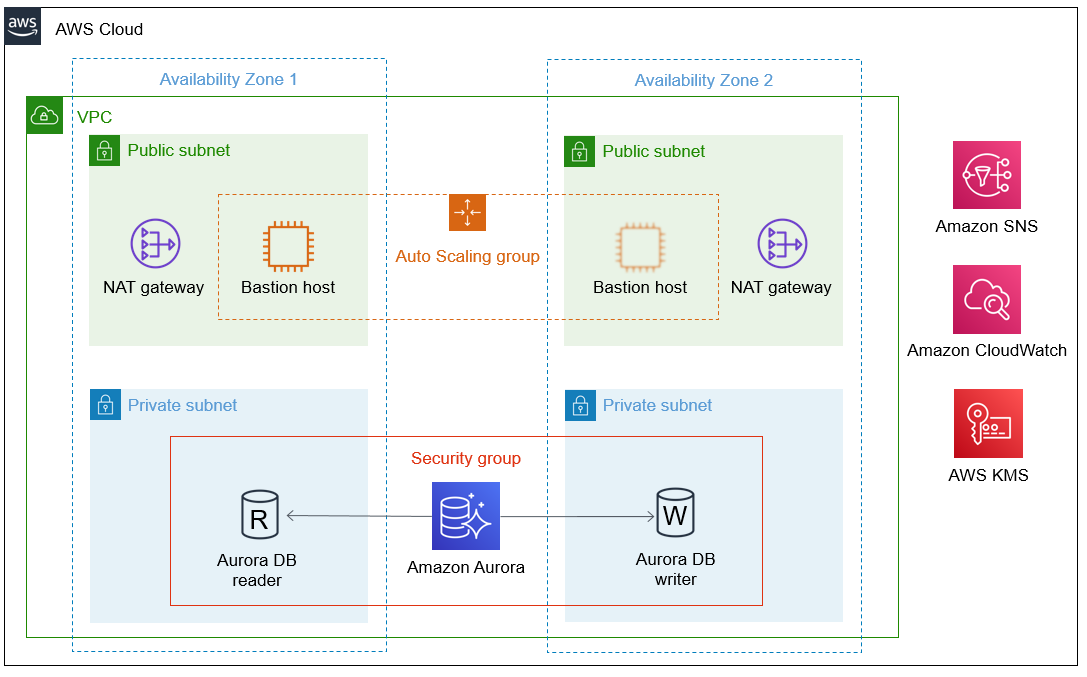
As shown in Figure 1, this Partner Solution sets up the following:
-
A highly available architecture that spans two Availability Zones.*
-
A virtual private cloud (VPC) configured with public and private subnets, according to AWS best practices, to provide you with your own virtual network on AWS.*
-
In the public subnets:
-
Managed network address translation (NAT) gateways to allow outbound internet access for resources in the private subnets.*
-
A Linux bastion host in an Auto Scaling group to allow inbound Secure Shell (SSH) access to resources in the private subnets.*
-
-
In the private subnets, an Aurora database (DB) cluster in a security group, including one DB reader and one DB writer.
-
An Amazon CloudWatch alarm to monitor the CPU on the bastion host and send alarm notifications using Amazon Simple Notification Service (Amazon SNS).
-
An encryption key using AWS Key Management Service (AWS KMS). The key enables encryption at rest for the Aurora DB cluster.
* The template that deploys this Partner Solution into an existing VPC skips the components marked by asterisks and prompts you for your existing VPC configuration.
Deployment options
This Partner Solution provides the following deployment options:
-
Deploy Aurora MySQL into a new VPC. This option builds a new AWS environment that consists of the VPC, subnets, NAT gateways, security groups, bastion hosts, and other infrastructure components. It then deploys Aurora MySQL into this new VPC.
-
Deploy Aurora MySQL into an existing VPC. This option provisions Aurora MySQL in your existing AWS infrastructure.
This Partner Solution provides separate templates for these options. It also lets you configure Classless Inter-Domain Routing (CIDR) blocks, instance types, and Aurora MySQL settings.
Predeployment steps
Requirements for deploying Aurora into an existing VPC
If you plan to deploy Aurora into an existing VPC, check the following:
-
Your VPC must have two private subnets in different Availability Zones for the database instances. This Partner Solution does not support shared subnets.
-
To download packages and software without exposing instances to the internet, the private subnets require NAT gateways in their route tables.
-
The domain name must be configured in the Dynamic Host Configuration Protocol (DHCP) options. For more information, see DHCP options sets.
-
You must have a Linux bastion host to run the tests discussed in the Test the deployment section. To install the bastion host, launch the AWS CloudFormation template that we provide for an existing subnet. When you launch the Partner Solution, you are prompted for your VPC settings.
If you don’t have an existing VPC that satisfies these requirements, use the new-VPC deployment option so that the Partner Solution builds a VPC for you in addition to deploying Aurora MySQL.
Deployment steps
-
Sign in to your AWS account, and launch this Partner Solution, as described under Deployment options. The AWS CloudFormation console opens with a prepopulated template.
-
Choose the correct AWS Region, and then choose Next.
-
On the Create stack page, keep the default setting for the template URL, and then choose Next.
-
On the Specify stack details page, change the stack name if needed. Review the parameters for the template. Provide values for the parameters that require input. For all other parameters, review the default settings and customize them as necessary. When you finish reviewing and customizing the parameters, choose Next.
Unless you’re customizing the Partner Solution templates or are instructed otherwise in this guide’s Predeployment section, don’t change the default settings for the following parameters: QSS3BucketName,QSS3BucketRegion, andQSS3KeyPrefix. Changing the values of these parameters will modify code references that point to the Amazon Simple Storage Service (Amazon S3) bucket name and key prefix. For more information, refer to the AWS Partner Solutions Contributor’s Guide. -
On the Configure stack options page, you can specify tags (key-value pairs) for resources in your stack and set advanced options. When you finish, choose Next.
-
On the Review page, review and confirm the template settings. Under Capabilities, select all of the check boxes to acknowledge that the template creates AWS Identity and Access Management (IAM) resources that might require the ability to automatically expand macros.
-
Choose Create stack. The stack takes about 30 minutes to deploy.
-
Monitor the stack’s status, and when the status is CREATE_COMPLETE, the Amazon Aurora MySQL Database deployment is ready.
-
To view the created resources, choose the Outputs tab.
Postdeployment steps
Test the deployment
To test the deployment, confirm that the MySQL database is accepting connections by following these steps. This optional test requires that you have bastion-host access with TCP forwarding capabilities (the parameters EnableBastion and EnableTCPForwarding are both set to "true").
-
Download the latest version of MySQL Workbench, and install it on the workstation from which you will be connecting to the Aurora MySQL DB cluster.
-
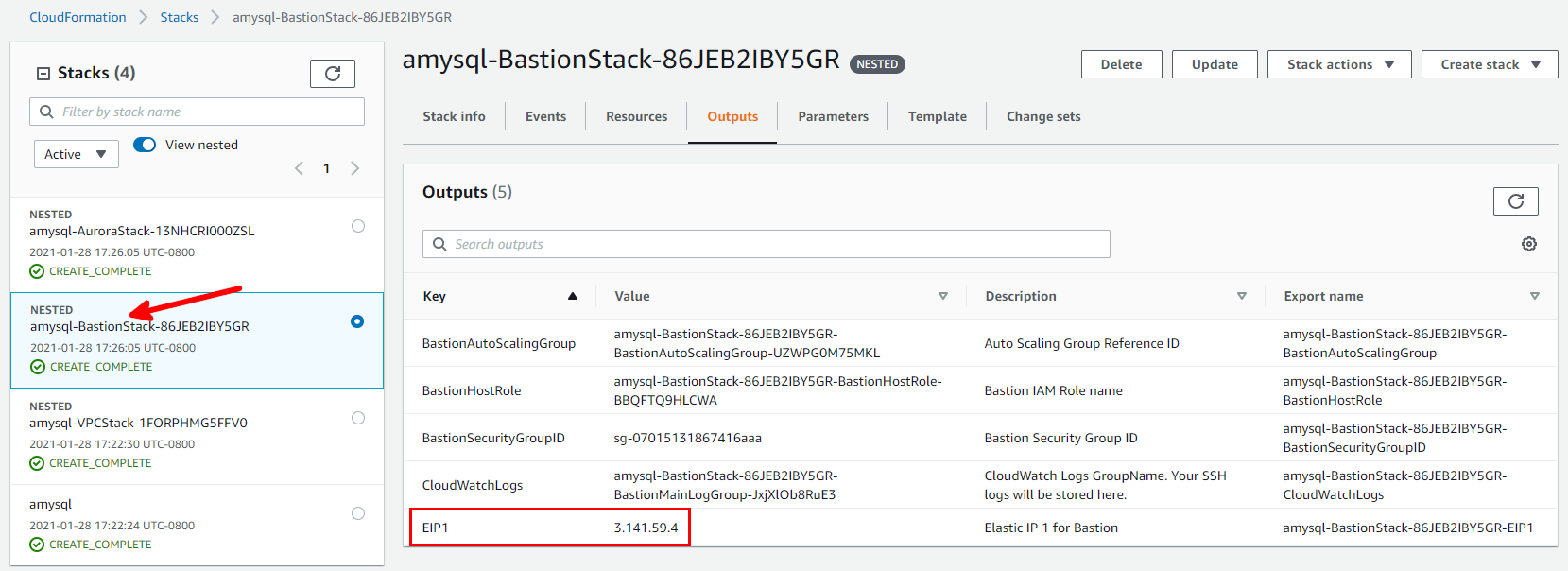
From the AWS CloudFormation console, on the BastionStack Outputs tab, note the value for
EIP1, as shown in Figure 2.
-
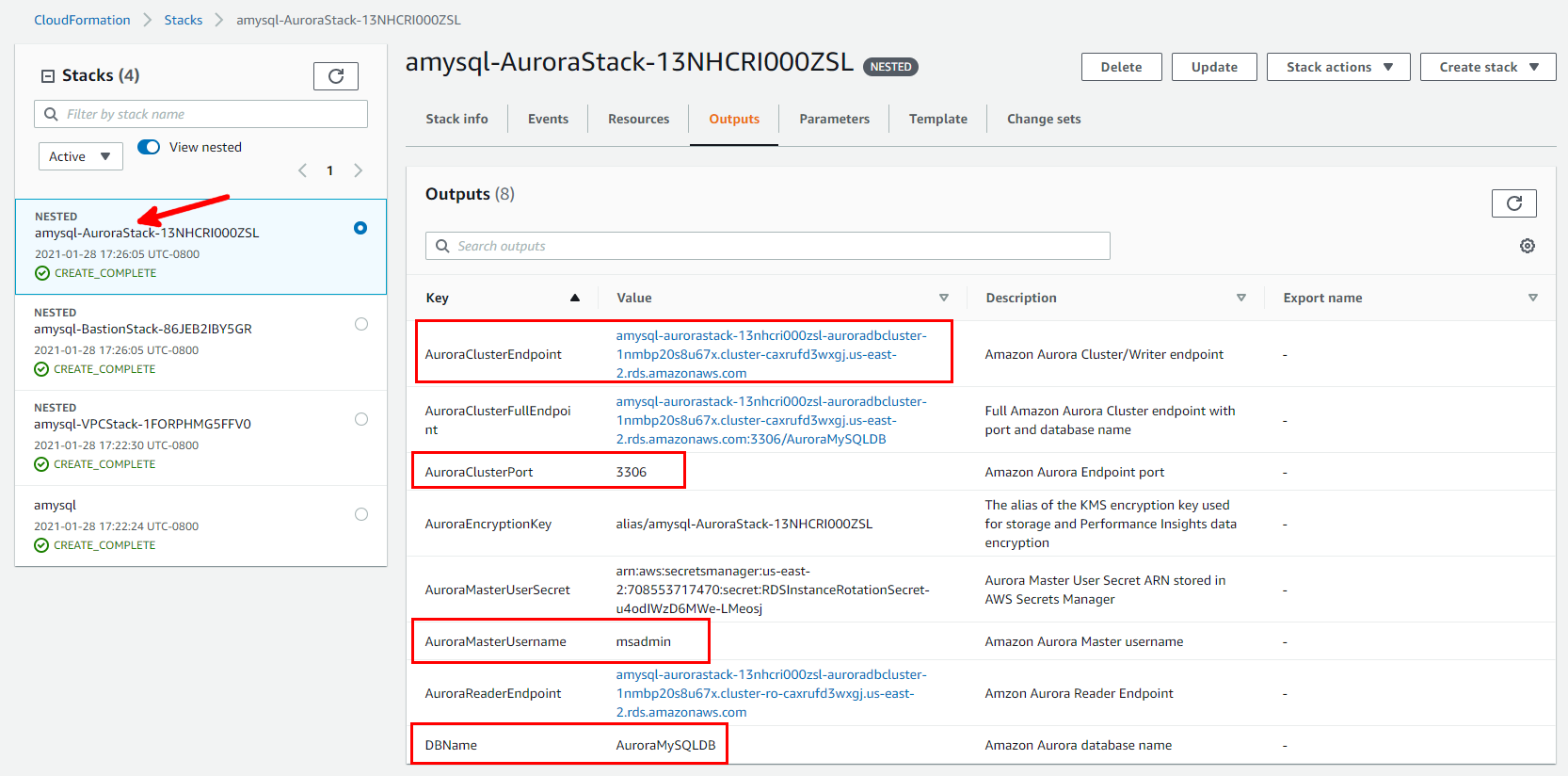
From the AWS CloudFormation console, on the AuroraStack Outputs tab, note the values of
DBName,DBMasterUsername,AuroraClusterEndpoint, andAuroraClusterPort, as shown in Figure 3.
-
Create an SSH tunnel to the bastion host using the following command, filling in the values for the bracketed terms. For <KeyPairName>, enter the path for the EC2 key pair that you specified for the
KeyPairNameparameter while creating the AWS CloudFormation stack.ssh -N -L <AuroraClusterPort>:<AuroraClusterEndpoint>:<AuroraClusterPort> ec2-user@EIP1 -i <KeyPairName>
A message appears indicating that you’ve connected to the bastion host.
-
Launch MySQL Workbench on your workstation.
-
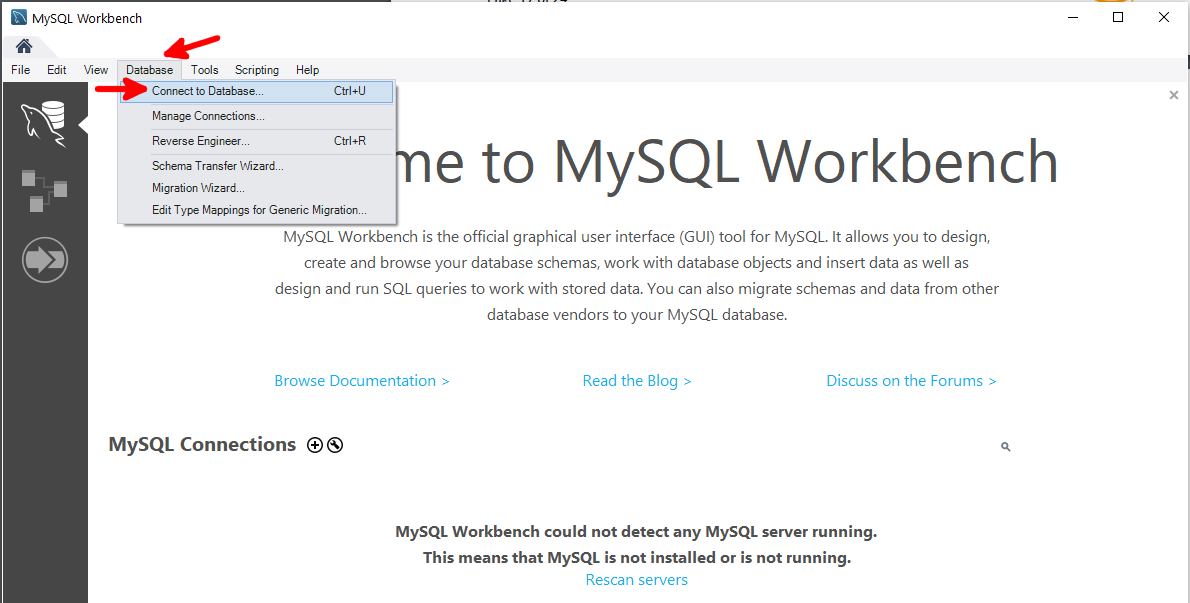
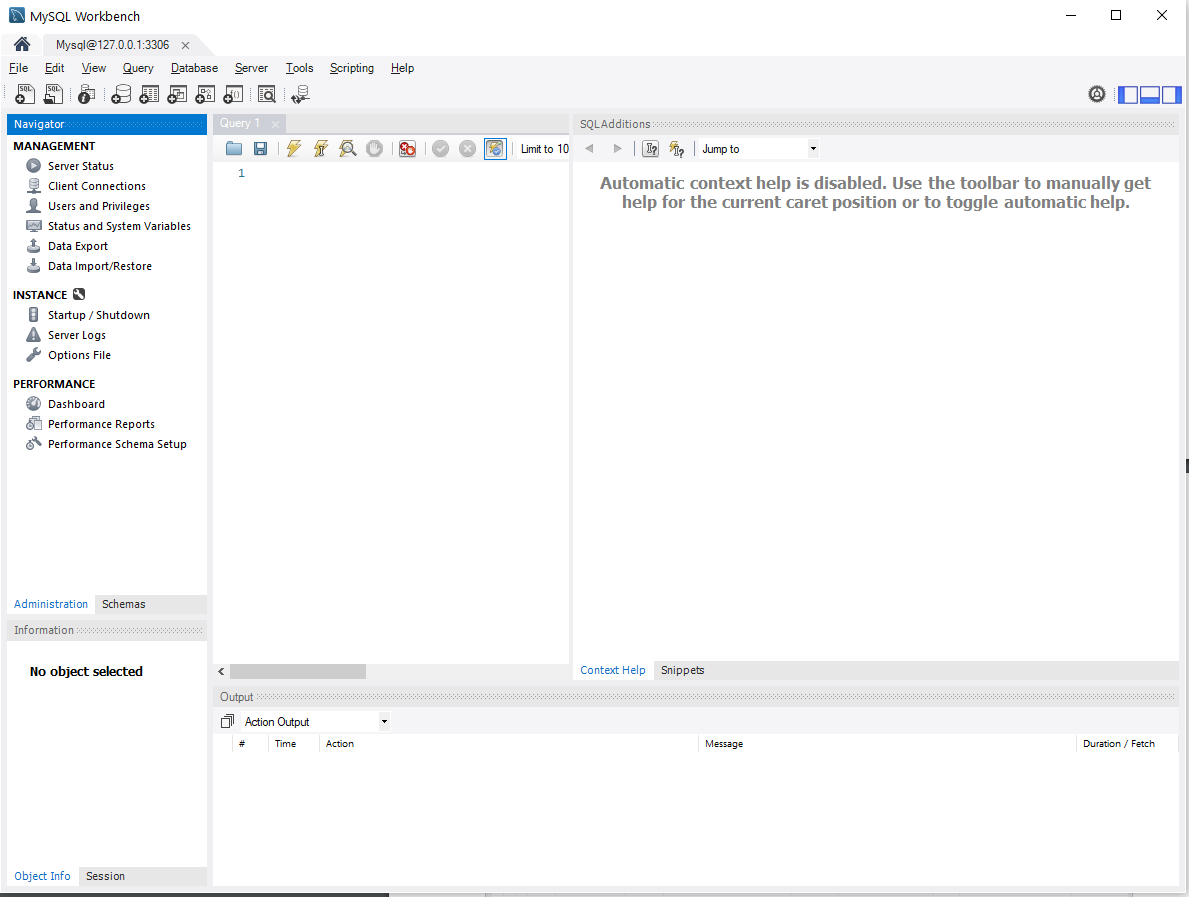
On the Database menu, choose Connect to Database, as shown in Figure 4.
-
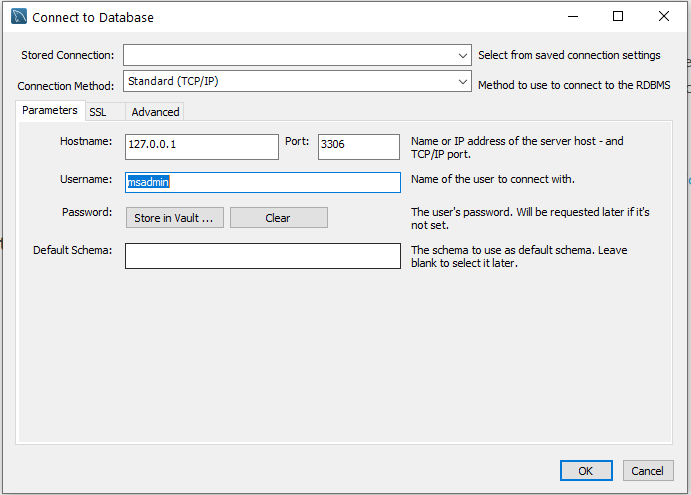
Enter the following in the Connect to Database dialog box, shown in Figure 5.
-
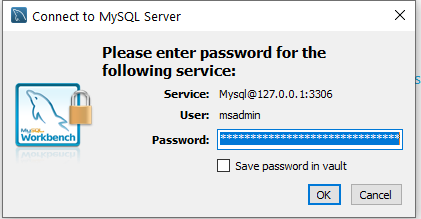
In the Connect to MySQL Server dialog box, shown in Figure 6, enter the administrator password (
DBMasterUserPassword) that you entered during stack creation. If theRotateDBPasswordparameter was set to true during stack creation, the administrator password for Aurora MySQL was rotated after creation. In this case, retrieve the new password as follows:-
From the AWS CloudFormation console, on the AuroraStack Outputs tab, note the values for
AuroraMasterUserSecret. -
On the AWS Secrets Manager console, choose the secret you noted above.
-
Choose Retrieve Secret Value, and copy the password.
A MySQL Workbench dashboard appears, as shown in Figure 7.
-
-
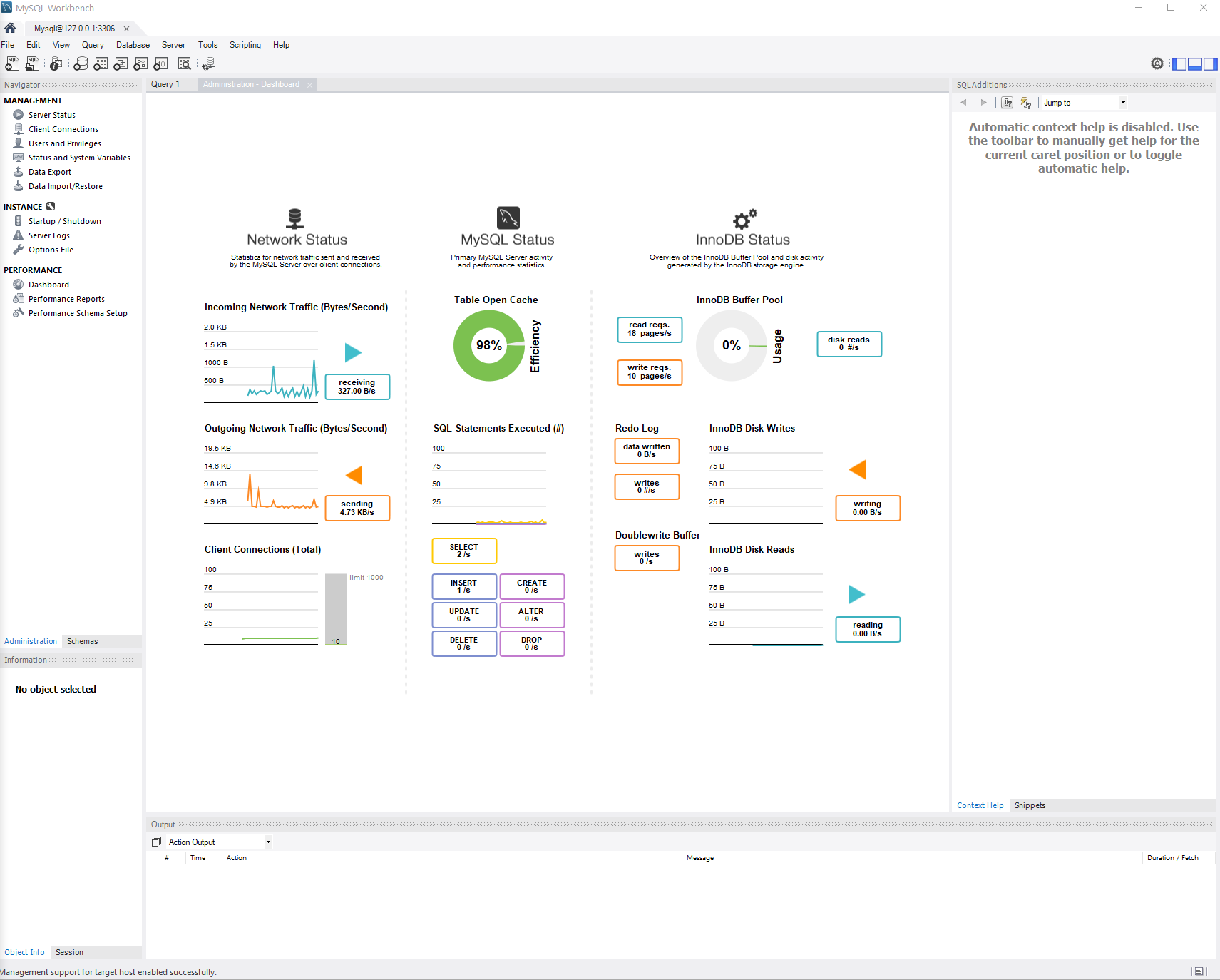
In the Navigator pane, under PERFORMANCE, choose Dashboard. Database-performance metrics appear, as shown in Figure 8.
-
Terminate the SSH tunnel by pressing Ctrl+C. You’ve completed the testing.
Troubleshooting
For troubleshooting common Partner Solution issues, refer to the AWS Partner Solution General Information Guide and Troubleshooting CloudFormation.
Customer responsibility
After you deploy a Partner Solution, confirm that your resources and services are updated and configured—including any required patches—to meet your security and other needs. For more information, refer to the Shared Responsibility Model.
Feedback
To submit feature ideas and report bugs, use the Issues section of the GitHub repository for this Partner Solution. To submit code, refer to the Partner Solution Contributor’s Guide. To submit feedback on this deployment guide, use the following GitHub links:
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS products or services, each of which is provided "as is" without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at https://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "as is" basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.