Duo Network Gateway on AWS
Partner Solution Deployment Guide

September 2020
Jacob Julian, Cisco Systems Inc.
Muffadal Quettawala, Amazon Web Services
Shivansh Singh, AWS Integration & Automation team

| Refer to the GitHub repository to view source files, report bugs, submit feature ideas, and post feedback about this Partner Solution. To comment on the documentation, refer to Feedback. |
This Partner Solution was created by Cisco Systems Inc. in collaboration with Amazon Web Services (AWS). Partner Solutions are automated reference deployments that help people deploy popular technologies on AWS according to AWS best practices. If you’re unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Overview
This guide covers the information you need to deploy the Duo Network Gateway Partner Solution in the AWS Cloud.
This Amazon Web Services (AWS) Partner Solution deploys Duo Network Gateway in the AWS Cloud. With Duo Network Gateway, users can securely access internal web applications from any device, using any browser, from anywhere in the world, without having to install or configure remote access software on their device. Users can remotely connect (via SSH) to configured hosts through Duo Network Gateway after installing Duo’s connectivity tool, providing server access without a virtual private network (VPN). This solution is for mulitple audiences, including IT architects, network administrators, DevOps professionals, and Duo instance owners who are planning to implement or extend their Duo Network Gateway deployment on the AWS Cloud. For more information, refer to the Duo Network Gateway documentation.
Costs and licenses
This Partner Solution requires a license for Duo Beyond. If you do not currently have a license for Duo Beyond, you can get a trial license at https://signup.duo.com/
The trial license of Duo Beyond gives you 30 days of free usage. After this time, you can upgrade to a production license by purchasing a subscription license of Duo Beyond.
Architecture
Deploying this Partner Solution with default parameters builds the following Duo Network Gateway environment in the AWS Cloud.
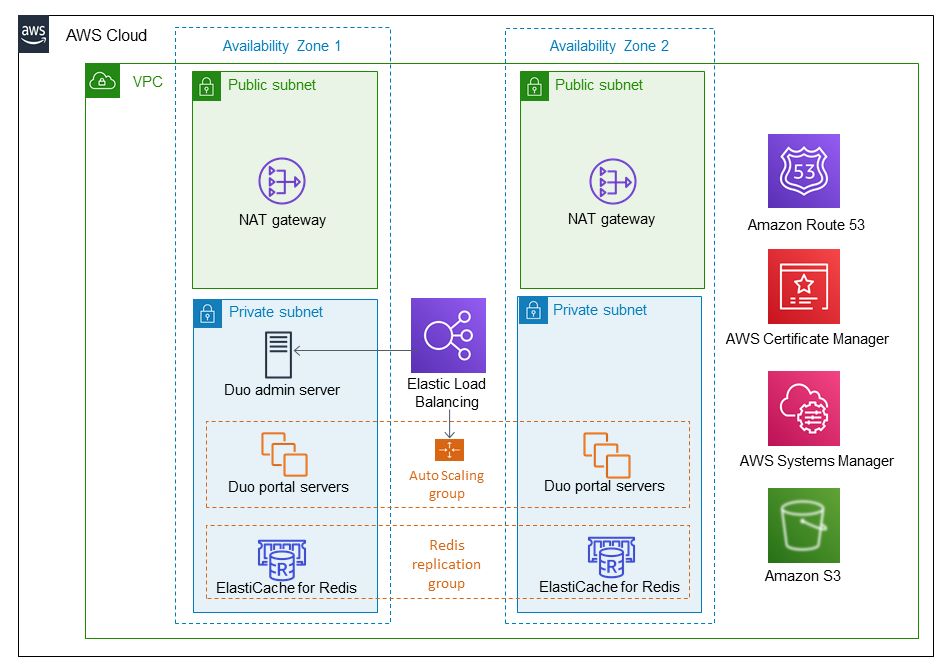
As shown in Figure 1, this Partner Solution sets up the following:
-
A highly available architecture that spans two Availability Zones.*
-
A VPC configured with public and private subnets, according to AWS best practices, to provide you with your own virtual network on AWS.*
-
In the public subnets, managed network address translation (NAT) gateways to allow outbound internet access for resources in the private subnets.*
-
In the private subnets:
-
Duo Network Gateway portal servers for providing end users access to the product interface.
-
A Duo Network Gateway admin server for completing configuration tasks.
-
An Amazon ElastiCache for Redis instance with a Redis replication group for storing the configuration for Duo Network Gateway.
-
-
Elastic Load Balancing for accepting incoming traffic for the Duo Network Gateway admin server and then distributing that traffic to the Duo Network Gateway portal servers using an AWS Auto Scaling group.
-
An Amazon Route 53 public hosted zone to route traffic for the Duo Network Gateway domain and its subdomains.
-
SSL/TSL certificates in AWS Certificate Manager (ACM) for the Duo Network Gateway portal and admin server load balancers.
-
AWS Systems Manager to manage access to the Duo Network Gateway portal and admin servers.
-
(Optional) Amazon Simple Storage Service (Amazon S3) bucket for Duo Network Gateway portal server scripted deployment.
* The template that deploys this Partner Solution into an existing VPC skips the components marked by asterisks and prompts you for your existing VPC configuration.
Deployment options
This Partner Solution provides the following deployment options:
-
Deploy Duo Network Gateway into a new VPC. This option builds a new AWS environment that consists of the VPC, subnets, NAT gateways, security groups, bastion hosts, and other infrastructure components. It then deploys Duo Network Gateway into this new VPC.
-
Deploy Duo Network Gateway into an existing VPC. This option provisions Duo Network Gateway in your existing AWS infrastructure.
This Partner Solution provides separate templates for these options. It also lets you configure Classless Inter-Domain Routing (CIDR) blocks, instance types, and Duo Network Gateway settings.
As an additional deployment option, you can upload a scripted configuration file for Duo Network Gateway at the time of deployment. This file must be generated according to Duo documentation. Once created, the file must be uploaded to an Amazon S3 bucket and specified during deployment using the 'ConfigYAMLPath' parameter. Typically, the scripted configuration option is used in automated workflows and command-line or programmatic methods of deploying this Quick Start. This supported scripted configuration is different than the scripted backup and restore feature, which is also supported by Duo Network Gateway.
Predeployment steps
This Partner Solution assumes that the user has:
-
A registered domain name e.g. mycompany.com that is registered externally or via AWS Route53.
-
A public hosted zone created in AWS Route53. In order to route internet traffic for a domain, AWS Route53 requires a public hosted zone to be created as a secondary step for either an external or AWS Route53 registered domain name.
Once the public hosted zone is created, the Partner Solution provides 2 deployment parameter options to the user:
Option1:
The user specifies the public hosted zone ID and subdomain names for the Duo Network Gateway admin and portal server load balancers as input parameters to the Partner Solution template. With this option, the Partner Solution subsequently generates tls certificates (in AWS ACM) and then creates resource records for the load balancer in the public hosted zone.
Option 2:
The user leaves the public hosted zone ID and subdomain parameters blank, but instead specifies the ARN(s) of certificates (either created by or imported in ACM) as input parameters to the Partner Solution template. In this option, the Partner Solution assumes that the user will manually provision the certificates and the resource record sets in the public hosted zone. The certificate ARN is used by the Partner Solution when creating the load balancer listeners.
Deployment steps
-
Sign in to your AWS account, and launch this Partner Solution, as described under Deployment options. The AWS CloudFormation console opens with a prepopulated template.
-
Choose the correct AWS Region, and then choose Next.
-
On the Create stack page, keep the default setting for the template URL, and then choose Next.
-
On the Specify stack details page, change the stack name if needed. Review the parameters for the template. Provide values for the parameters that require input. For all other parameters, review the default settings and customize them as necessary. When you finish reviewing and customizing the parameters, choose Next.
Unless you’re customizing the Partner Solution templates or are instructed otherwise in this guide’s Predeployment section, don’t change the default settings for the following parameters: QSS3BucketName,QSS3BucketRegion, andQSS3KeyPrefix. Changing the values of these parameters will modify code references that point to the Amazon Simple Storage Service (Amazon S3) bucket name and key prefix. For more information, refer to the AWS Partner Solutions Contributor’s Guide. -
On the Configure stack options page, you can specify tags (key-value pairs) for resources in your stack and set advanced options. When you finish, choose Next.
-
On the Review page, review and confirm the template settings. Under Capabilities, select all of the check boxes to acknowledge that the template creates AWS Identity and Access Management (IAM) resources that might require the ability to automatically expand macros.
-
Choose Create stack. The stack takes about 15 minutes to deploy.
-
Monitor the stack’s status, and when the status is CREATE_COMPLETE, the Duo Network Gateway deployment is ready.
-
To view the created resources, choose the Outputs tab.
Postdeployment steps
After the Partner Solution has been successfully created, you can interact with Duo Network Gateway from a web browser. Perform the following steps:
-
In a browser, navigate to https://<URL-of-the-network-gateway-load-balancer>:8443 from a network in the 'AdminServerRemoteAccessCIDR' subnet, and log in to the Duo Network Gateway admin console. Your browser warns you about an untrusted certificate the first time you access the page. Dismiss the warning and continue to the page.
-
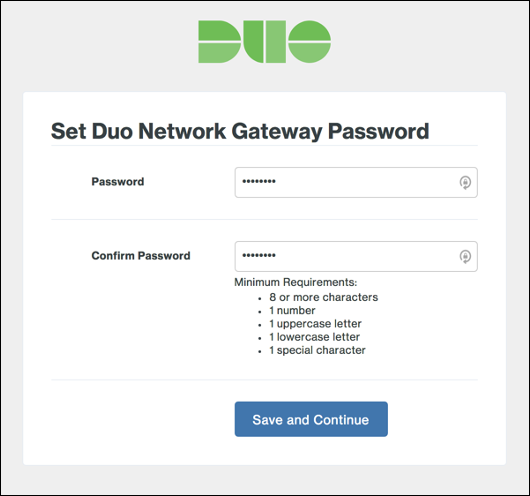
On the first page of the Duo Network Gateway configuration screen, choose a password for the Duo Network Gateway admin console. After entering a password that meets the requirements, choose Save and Continue.
-
On the Make Duo Network Gateway visible to the internet page, either fill in the fields, as shown in the following image, or choose the Already have a Duo Network Gateway configuration file? Import it now link to import a configuration file.
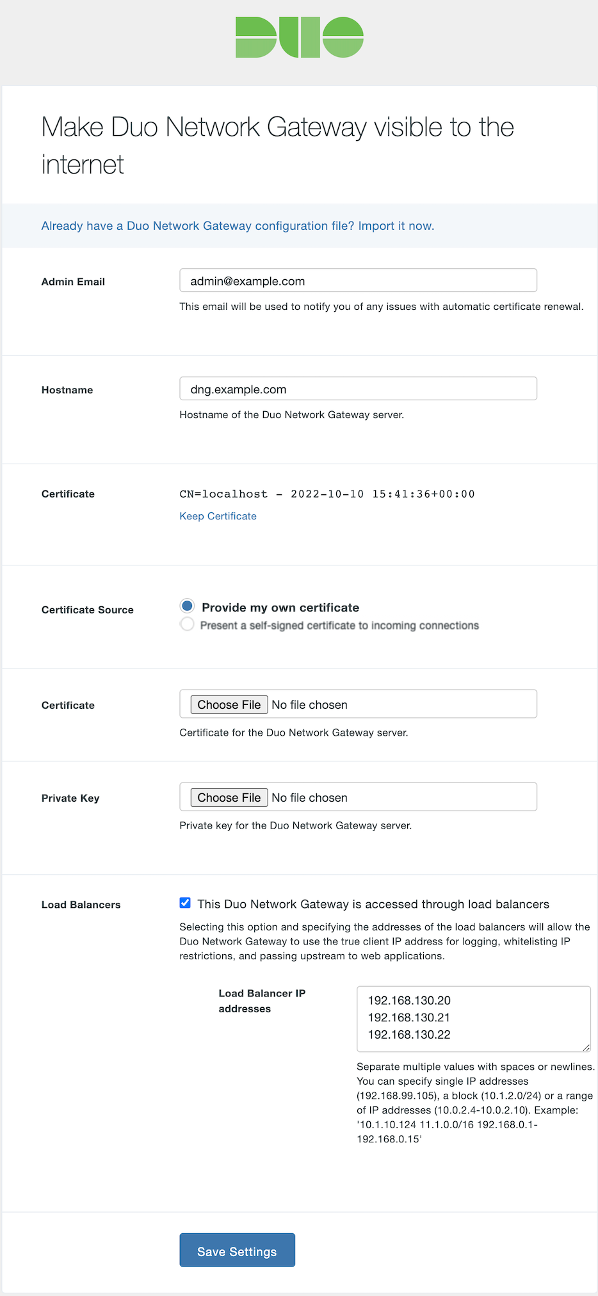
Note the following recommendations when filling in the fields:
-
As this Partner Solution uses load balancers that present SSL security to end users, you can use a certificate for the connection between the load balance and Duo Network Gateway. There are two options for providing this certificate:
-
If you want to provide your own SSL certificate for Duo Network Gateway, choose Change Certificate and select Provide my own certificate.
-
If you want to use self-signed certificates for the Duo Network Gateway server, choose the Present a self-signed certificate to incoming connections option.
-
-
After selecting the This Duo Network Gateway is accessed through load balancers check box, specify the internal IP addresses of your Duo Network Gateway portal server load balancer, which you can locate in the Outputs section of the Partner Solution. This setting makes the Duo Network Gateway aware of the load balancer IP addresses, which allows the source client IP addresses to log information, apply allowed IP restrictions, and pass IP addresses to protected applications.
-
Be sure to provide complete and accurate information on this page to avoid errors with the initial configuration. If an error occurs, you will need to re-enter the information again before proceeding, including selecting the certificate and key.
-
When you choose Save and Continue, you are redirected to the Duo Network Gateway admin console, where you can add a SAML authentication source and configure Duo Network Gateway to proxy the applications for adding Duo policies.
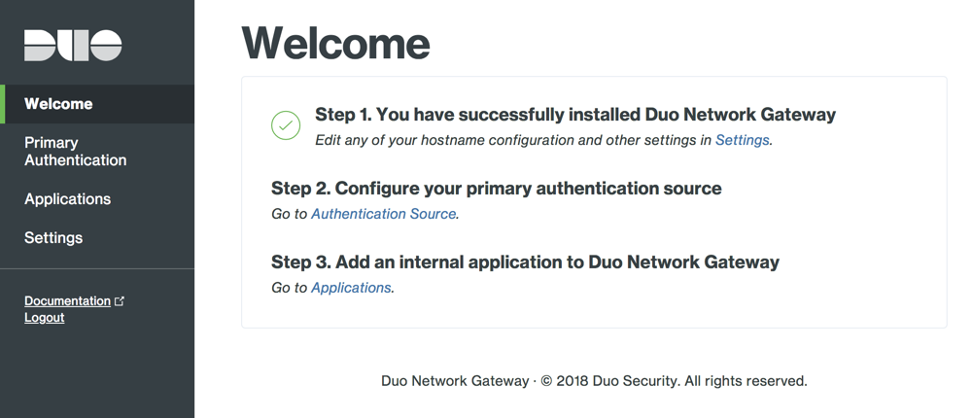
For additional information, access the Duo documentation.
Security
The Partner Solution exposes two user-configurable security group access parameters: 'AdminServerRemoteAccessCIDR' and 'PortalServerRemoteAccessCIDR'. Be sure that the 'AdminServerRemoteAccessCIDR' parameter 'is accessible only on authorized network ranges for both ports 22 and 8443, not widely accessible on the internet.
Troubleshooting
For troubleshooting common Partner Solution issues, refer to the AWS Partner Solution General Information Guide and Troubleshooting CloudFormation.
Resources
For a list of common error messages with descriptions and resolutions, see the official Duo Security Knowledge Base.
Customer responsibility
After you deploy a Partner Solution, confirm that your resources and services are updated and configured—including any required patches—to meet your security and other needs. For more information, refer to the Shared Responsibility Model.
Feedback
To submit feature ideas and report bugs, use the Issues section of the GitHub repository for this Partner Solution. To submit code, refer to the Partner Solution Contributor’s Guide. To submit feedback on this deployment guide, use the following GitHub links:
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS products or services, each of which is provided "as is" without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at https://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "as is" basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.