PCI DSS and AWS Foundational Security Best Practices on AWS
Partner Solution Deployment Guide

February 2021
Kanishk Mahajan and Andrew Glenn, AWS Integration & Automation team

| Refer to the GitHub repository to view source files, report bugs, submit feature ideas, and post feedback about this Partner Solution. To comment on the documentation, refer to Feedback. |
This Partner Solution was created by Amazon Web Services (AWS). Partner Solutions are automated reference deployments that help people deploy popular technologies on AWS according to AWS best practices. If you’re unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Overview
This guide covers the information you need to deploy the PCI DSS and AWS Foundational Security Best Practices Partner Solution in the AWS Cloud.
This reference deployment guide provides instructions for deploying Payment Card Industry Data Security Standard (PCI DSS) and AWS Foundational Security Best Practices (AWS FSBP) on the AWS Cloud using AWS CloudFormation templates.
Costs and licenses
No software licenses are necessary to use this solution.
There is no cost to use this Partner Solution, but you will be billed for any AWS services or resources that this Partner Solution deploys. For more information, refer to the AWS Partner Solution General Information Guide.
Architecture
Deploying this Partner Solution with default parameters builds the following PCI DSS and AWS FSBP environment in the AWS Cloud.
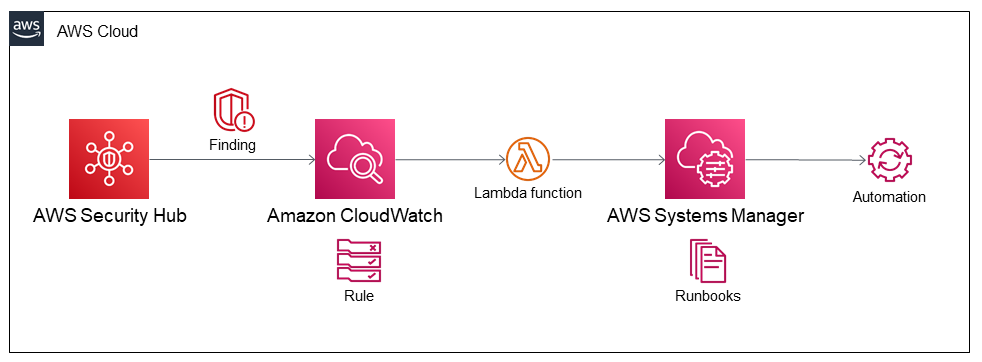
As shown in Figure 1, this Partner Solution sets up the following:
-
AWS Security Hub to compile findings of automated and continuous evaluations of PCI DSS and AWS FSBP controls against your AWS resources. Custom actions in Security Hub send findings to Amazon CloudWatch as custom events.
-
Amazon CloudWatch to match a custom event from AWS Security Hub with a rule that triggers an AWS Lambda function.
-
AWS Lambda functions to invoke the appropriate AWS Systems Manager runbook to remediate a finding of a deviation from PCI DSS and AWS FSBP controls.
-
AWS Systems Manager to perform the automated remediation actions defined in runbooks.
Deployment options
This Partner Solution provides automation to remediate deviations from the following sets of industry controls:
-
Payment Card Industry Data Security Standard (PCI DSS)
-
AWS Foundational Security Best Practices
PCI DSS and AWS FSBP remediations are each packaged in two templates. To deploy PCI DSS, choose the link to launch the first PCI DSS template and follow steps 1–8 provided. After deploying the first template, choose the link to launch the second PCI DSS template and repeat steps 1–8. Repeat this entire process to deploy the two AWS FSBP templates.
Predeployment steps
-
Ensure that AWS Config is turned on and recording all supported resources, including global resources, in all accounts and Regions where Security Hub is enabled. Security Hub uses service-linked AWS Config rules. You are not charged by AWS Config for these service-linked rules. you are only charged according to AWS Security Hub pricing.
-
Ensure that Security Hub is enabled in the account and Region where these templates are deployed.
-
This Partner Solution uses a KMS key to remediate the PCI.CloudTrail.1 control. The key must have permissions to encrypt/decrypt AWS CloudTrail logs in the AWS account in which this Partner Solution is deployed. Make sure you update the key policy with the AWS account ID. To do this, search for a key with an alias of "PCI-CMK" in the AWS KMS console. Then, see Required CMK policy sections for use with CloudTrail for instructions to enable CloudTrail log encrypt and decrypt permissions.
Deployment steps
-
Sign in to your AWS account, and launch this Partner Solution, as described under Deployment options. The AWS CloudFormation console opens with a prepopulated template.
-
Choose the correct AWS Region, and then choose Next.
-
On the Create stack page, keep the default setting for the template URL, and then choose Next.
-
On the Specify stack details page, change the stack name if needed. Review the parameters for the template. Provide values for the parameters that require input. For all other parameters, review the default settings and customize them as necessary. When you finish reviewing and customizing the parameters, choose Next.
Unless you’re customizing the Partner Solution templates or are instructed otherwise in this guide’s Predeployment section, don’t change the default settings for the following parameters: QSS3BucketName,QSS3BucketRegion, andQSS3KeyPrefix. Changing the values of these parameters will modify code references that point to the Amazon Simple Storage Service (Amazon S3) bucket name and key prefix. For more information, refer to the AWS Partner Solutions Contributor’s Guide. -
On the Configure stack options page, you can specify tags (key-value pairs) for resources in your stack and set advanced options. When you finish, choose Next.
-
On the Review page, review and confirm the template settings. Under Capabilities, select all of the check boxes to acknowledge that the template creates AWS Identity and Access Management (IAM) resources that might require the ability to automatically expand macros.
-
Choose Create stack. The stack takes about 20 minutes to deploy.
-
Monitor the stack’s status, and when the status is CREATE_COMPLETE, the PCI DSS and AWS Foundational Security Best Practices deployment is ready.
-
To view the created resources, choose the Outputs tab.
Postdeployment steps
Test the deployment
Security Hub begins running security checks within two hours after you deploy PCI DSS and AWS FSBP controls. After the initial check, subsequent checks occur on a periodic or change-triggered basis, depending on the control. For more information, see Schedule for running security checks. Follow the steps in this section to test the deployment.
The following steps test remediation of the PCI EC2.2 control. This control states that the VPC default security group should prohibit inbound and outbound traffic, and it is evaluated on a change-triggered basis. To test it, purposefully misconfigure security group settings in the Amazon EC2 console to allow inbound traffic. This should trigger a Security Hub finding which remediates the security issue by undoing the misconfiguration in the console.
-
Choose Security Groups in the Amazon EC2 console.
-
Choose the Security group ID of the default VPC.
-
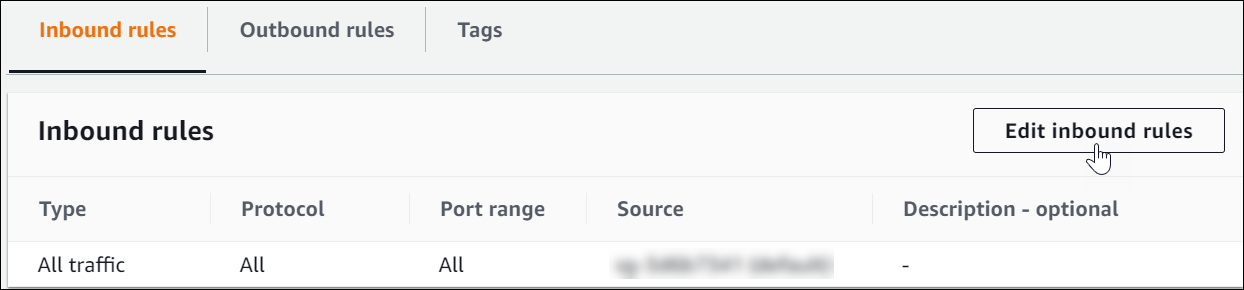
Choose Edit inbound rules.
-
Select Add rule.
-
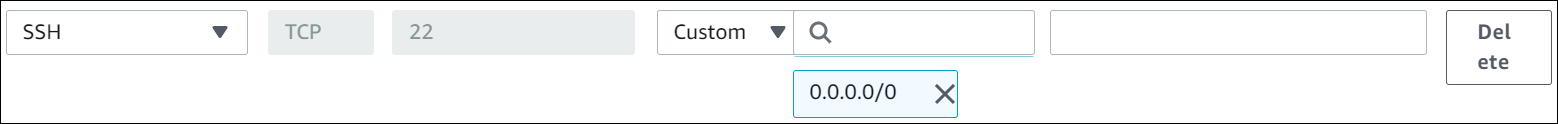
Select SSH as the Type and 0.0.0.0/0 as the Source.
-
Select Save rules. Make a note of the security group Amazon Resource Number (ARN).
-
In Security Hub, select Findings. Locate the finding that corresponds to the misconfiguration.
-
Select the check box next to the finding and select Actions.
-
Select PCI EC2.2 from the drop-down list. A message displays that findings were successfully sent to AWS CloudWatch Events.
-
In Systems Manager, select Automation. You should see a successful automation execution that corresponds to the PCI EC2.2 remediation.
-
To confirm success of the remediation, select Security Groups in the Amazon EC2 console. Then select the Security group ID of the default VPC. Confirm that the SSH rule is removed from the Inbound rules tab.
| For more information on the format of Security Hub findings, see Results of security checks. |
AWS Security Best Practices
AWS categorizes each Security Hub service action into one of five access levels: list, read, write, permissions management, or tagging. To allow a large group of users to access list and read Security Hub actions, and only a small group to access the write action, use managed IAM policies. For more information, see Security best practices in IAM.
Security Hub ingests findings generated from integrated providers (both third-party services using ASFF.
Security
This Partner Solution follows security best practices and guidelines as documented in Security in AWS Security Hub.
Troubleshooting
For troubleshooting common Partner Solution issues, refer to the AWS Partner Solution General Information Guide and Troubleshooting CloudFormation.
Customer responsibility
After you deploy a Partner Solution, confirm that your resources and services are updated and configured—including any required patches—to meet your security and other needs. For more information, refer to the Shared Responsibility Model.
Feedback
To submit feature ideas and report bugs, use the Issues section of the GitHub repository for this Partner Solution. To submit code, refer to the Partner Solution Contributor’s Guide. To submit feedback on this deployment guide, use the following GitHub links:
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS products or services, each of which is provided "as is" without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at https://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "as is" basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.