Cisco Duo MFA on AWS
Partner Solution Deployment Guide

June 2022
Nagmesh Kumar, AWS Professional Services team
Dave May, Troy Ameigh, & Troy Lindsay, AWS Integration & Automation team

| Refer to the GitHub repository to view source files, report bugs, submit feature ideas, and post feedback about this Partner Solution. To comment on the documentation, refer to Feedback. |
This Partner Solution was created by Duo Security (a wholly owned subsidiary of Cisco) in collaboration with Amazon Web Services (AWS). Partner Solutions are automated reference deployments that help people deploy popular technologies on AWS according to AWS best practices. If you’re unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Overview
This Partner Solution deploys Cisco Duo MFA to the AWS Cloud. If you are unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Security
| On May 26, 2022, Duo released version 5.7.1 of the Duo Authentication Proxy. This includes patches for two vulnerabilities that are described in the following points. |
Duo has fixed the following IP address vulnerabilities by updating Python to version 3.8.12 and replacing its third-party library with the IPv4/IPv6 manipulation library. For more information, refer to Authentication Proxy—Release Notes.
-
A vulnerability mishandles IP address strings. For more information, refer to CVE-2021-29921 Detail.
-
A vulnerability improperly computes hash values in
IPv4InterfaceandIPv6Interfaceclasses. For more information, refer to CVE-2020-14422 Detail.
A vulnerability of Twisted version 21.2.0 remains unresolved for Authentication Proxy 5.7.1. This vulnerability parses HTTP requests without validating that the requests conform to RFC 7230. The Authentication Proxy is only vulnerable to this exploit if it’s configured to use http_proxy. For more information, refer to CVE-2022-24801. Duo is upgrading Twisted to version 22, but version 21.2.0 remains a high risk until a fix is released, which will be announced in the Duo Community Release Notes.
|
Python library (python-cryptography) version 3.2 is vulnerable to Bleichenbacher timing attacks. This vulnerability remains for Authentication Proxy 5.7.1, but the Duo team has confirmed that Authentication Proxy doesn’t use vulnerable RSA (Rivest-Shamir-Adleman) decryption API code and has concluded that the Authentication Proxy is not exposed to this vulnerability. For more information, refer to CVE-2020-25659 Detail.
|
Additional security resources
To take advantage of Duo’s security fixes and latest features, run the latest software version. To determine the version of your Authentication Proxy, refer to How do I determine my installed Duo Authentication Proxy application version? If you use the Authentication Proxy version included in Duo + Amazon Web Services, you are running the latest version. For more information, refer to the following resources:
Costs and licenses
There is no cost to use this Partner Solution, but you will be billed for any AWS services or resources that this Partner Solution deploys. For more information, refer to the AWS Partner Solution General Information Guide. Additionally, this Partner Solution requires a license for Duo MFA. For more information, see Duo Editions & Pricing.
Architecture
Deploying this Partner Solution for a new virtual private cloud (VPC) with default parameters builds the following Duo MFA environment in the AWS Cloud.
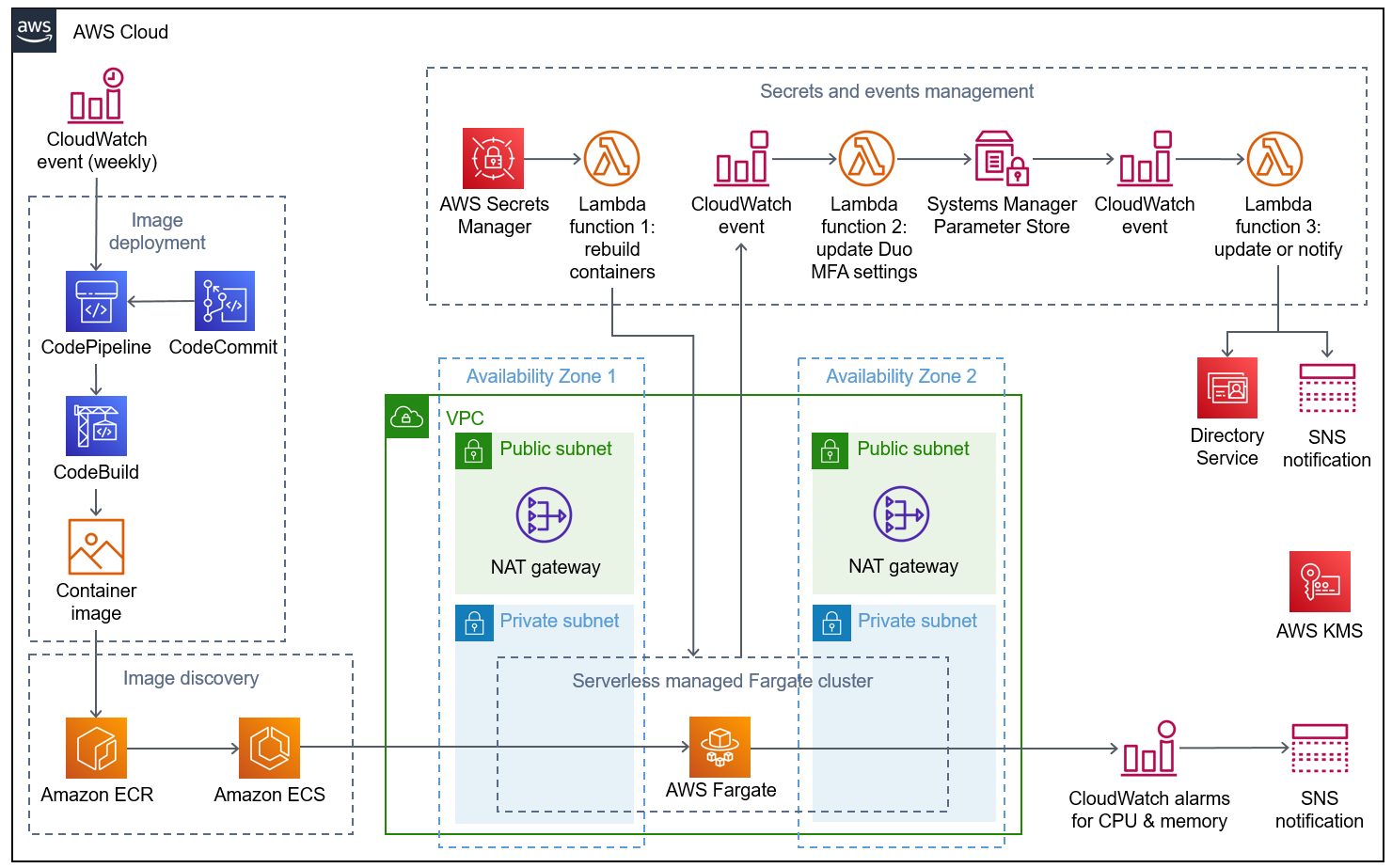
As shown in Figure 1, this Partner Solution sets up the following:
-
A highly available architecture that spans two Availability Zones.*
-
A VPC configured with public and private subnets, according to AWS best practices, to provide you with your own virtual network on AWS.*
-
In the public subnets, managed network address translation (NAT) gateways to allow outbound internet access for resources in the private subnets.*
-
A serverless managed AWS Fargate cluster with containers for Duo Authentication Proxy. The cluster is replaced whenever a new image is deployed or whenever the secrets are updated.
-
-
A continuous integration and continuous delivery (CI/CD) pipeline for image deployment:
-
AWS CodePipeline to retrieve the latest code from AWS CodeCommit in response to an Amazon CloudWatch event once a week. You can change this frequency in the AWS CloudFormation parameter
EcrCronExpressionwhen you create or update the stack. -
AWS CodeBuild, which CodePipeline uses to build a new container image. CodePipeline then uploads the new container image to Amazon Elastic Container Registry (Amazon ECR).
-
-
Image discovery:
-
Amazon ECR, which is configured to scan on push. Amazon ECR stores each new container image. CodeBuild jobs can wait for the results of the scan before completing.
-
Amazon Elastic Container Service (Amazon ECS), which discovers the images and pushes them to Fargate. Application Auto Scaling automatically scales the Amazon ECS tasks when CPU or memory limits are reached. Scaling accommodates spikes in traffic, such as early morning logins. Similarly, when Amazon ECS does not see much activity, Application Auto Scaling decreases the number of tasks. It then initiates the workflow to get IP addresses from Lambda functions and update the AWS Directory Service RADIUS configuration.
-
-
CloudWatch CPU and memory alarms that invoke Amazon Simple Notification Service (Amazon SNS) notifications to Duo administrators when Fargate containers scale workloads up or down, when a new container is built, or when a container build fails.
-
An AWS Key Management Service (AWS KMS) key that encrypts all Duo Authentication Proxy-related resources.
-
Secrets and events management, which works as follows (a two- to three-minute process):
-
AWS Secrets Manager rotates the secrets that are used for the cluster.
-
With each rotation, an AWS Lambda function replaces the Fargate containers, deploying the newest image.
-
After the Fargate containers stabilize, a CloudWatch event initiates a second Lambda function. This function updates the Duo MFA settings in AWS Systems Manager Parameter Store, which stores the latest Fargate container IP addresses. Specifically, this Lambda function finds the IP address of the Fargate task and updates the Systems Manager parameter
DuoServiceIps. -
Finally, a CloudWatch event initiates a third Lambda function. This function either updates the RADIUS IP address in AWS Directory Service or, if the update fails, sends Duo administrators an SNS notification.
-
*The template that deploys the Partner Solution into an existing VPC skips the components marked by asterisks and prompts you for your existing VPC configuration.
Deployment options
This Partner Solution provides the following deployment options:
-
Deploy Duo MFA into a new VPC. This option builds a new AWS environment that consists of the VPC, subnets, NAT gateways, security groups, bastion hosts, and other infrastructure components. It then deploys Duo MFA into this new VPC.
-
Deploy Duo MFA into an existing VPC. This option provisions Duo MFA in your existing AWS infrastructure.
This Partner Solution provides separate templates for these options. It also lets you configure Classless Inter-Domain Routing (CIDR) blocks, instance types, and Duo MFA settings.
Predeployment steps
You must set up at least one Duo user whose email address is associated with at least one user in Microsoft Active Directory.
Prepare your Duo account
-
If you don’t already have a Duo account, sign up for one.
-
Log in to the Duo administrator panel.
-
Accounts other than federal: https://admin.duosecurity.com/login
-
Federal accounts: https://admin.duofederal.com
-
-
Navigate to Applications.
-
Obtain the integration key, secret key, and API hostname. You will enter these three items as template parameter values when you deploy this Partner Solution.
-
If directory synchronization is not required, do the following:
-
Choose Protect an Application.
-
In the applications list, locate the entry for AWS Directory Services by searching for AWS Partner Solution. On the far right, choose Protect.
-
Configure the application, and get your integration key, secret key, and API hostname. Write down these three items. For details, see Protecting Applications.
-
-
If directory synchronization is required, do the following:
-
Set up directory synchronization by following the steps in Synchronizing Users from Active Directory.
-
From the Duo administrator panel, choose Users. Then choose Directory Sync, New Directory, On-Premises Active Directory (even if AWS Managed Microsoft AD).
-
Enter a directory name (which you need to identify the directory in Duo), the host IPs, and the port. (You can enter the other IP and port for the second domain controller as part of configuring directory synchronization.)
-
For Authentication Type, choose NTLMv2. Enter the base DN (distinguished name) following the instructions.
-
If needed, change other settings.
-
Choose Add Directory.
-
After the screen refreshes, scroll to the bottom, where you see the integration key, secret key, and API hostname. Write down these three items.
-
-
Deployment steps
-
Sign in to your AWS account, and launch this Partner Solution, as described under Deployment options. The AWS CloudFormation console opens with a prepopulated template.
-
Choose the correct AWS Region, and then choose Next.
-
On the Create stack page, keep the default setting for the template URL, and then choose Next.
-
On the Specify stack details page, change the stack name if needed. Review the parameters for the template. Provide values for the parameters that require input. For all other parameters, review the default settings and customize them as necessary. When you finish reviewing and customizing the parameters, choose Next.
Unless you’re customizing the Partner Solution templates or are instructed otherwise in this guide’s Predeployment section, don’t change the default settings for the following parameters: QSS3BucketName,QSS3BucketRegion, andQSS3KeyPrefix. Changing the values of these parameters will modify code references that point to the Amazon Simple Storage Service (Amazon S3) bucket name and key prefix. For more information, refer to the AWS Partner Solutions Contributor’s Guide. -
On the Configure stack options page, you can specify tags (key-value pairs) for resources in your stack and set advanced options. When you finish, choose Next.
-
On the Review page, review and confirm the template settings. Under Capabilities, select all of the check boxes to acknowledge that the template creates AWS Identity and Access Management (IAM) resources that might require the ability to automatically expand macros.
-
Choose Create stack. The stack takes about 45 minutes to deploy.
-
Monitor the stack’s status, and when the status is CREATE_COMPLETE, the Cisco Duo MFA deployment is ready.
-
To view the created resources, choose the Outputs tab.
Postdeployment steps
After you launch the stack, verify your deployment and, if desired, modify your implementation, as described in the following sections.
Verify your deployment
-
Verify that the Amazon ECS cluster contains the number of instances that you want.
-
Open the Amazon ECS console.
-
In the left pane, choose Clusters.
-
Choose the ECS Instances tab.
-
-
Verify the MFA configuration.
-
Open the Directory Service console.
-
Select your directory.
-
Choose the Networking & security tab.
-
Find the Multi-factor authentication pane at the bottom of the page.
-
Verify that the RADIUS status is Completed. You may need to wait for the status to appear; Systems Manager can take a few minutes to register and configure the instances. If the status is Failed, see the Troubleshooting section of this guide.
-
Verify that the configuration otherwise looks as you expect. To change anything, choose Actions, Edit. (The RADIUS instances' IP addresses were generated by an AWS Fargate task. The shared secret code values are empty for security reasons.)
-
-
Verify that MFA is working in an Amazon WorkSpaces client.
-
Open the Amazon WorkSpaces client.
-
Under the username and password boxes, in the third text box, enter the MFA code from the Duo Mobile app or the hardware security token mentioned earlier.
-
-
If you chose directory synchronization earlier, synchronize users to Duo Cloud, and add hardware tokens.
-
Open the Duo administrator panel. Choose Users on the left side of screen, and choose Directory Sync near the top right.
-
Enter the NTLM (Active Directory) domain and the NTLM workstation: the hostname of one of the Duo RADIUS ECS IP addresses (example: 10.0.10.10, 10.0.11.10).
-
At the bottom of the page, choose Refresh. This brings you to the top of the page, which instructs you to select a group to import.
-
At the bottom of the page, for Groups, enter the Active Directory user group you want to import into Duo. Choose Save Groups.
-
At the top of the page, select Sync Now.
-
On the left, choose Users. Review the user list that was imported from your Active Directory group. You should see details about the users that were imported from Active Directory as well as Duo-specific details.
-
Add hardware tokens. To do so, select a user, choose Add Hardware Token, enter the serial number of one of the tokens that you ordered, and then choose Attach Hardware Token.
-
-
Update user settings for each user.
-
From the Duo administrator panel, choose Users on the left side of the screen, and select a user.
-
Choose the status—either Active or Bypass—to determine whether to require MFA when that user logs in.
-
(Optional) Add a phone number so that the user can use the Duo Mobile app.
-
Modify your implementation
If you want to increase or decrease the number of RADIUS tasks after deploying the Partner Solution, update the AWS CloudFormation stack and specify the desired number of servers. Then perform a stack update. If you increase the number of tasks, the Amazon ECS service starts up that number of new tasks and installs and configures the Duo Authentication Proxy service for each.
-
Open the AWS CloudFormation console.
-
Choose your deployed Duo stack, and choose Update.
-
Choose Use current template.
-
Under Specify stack details section, find
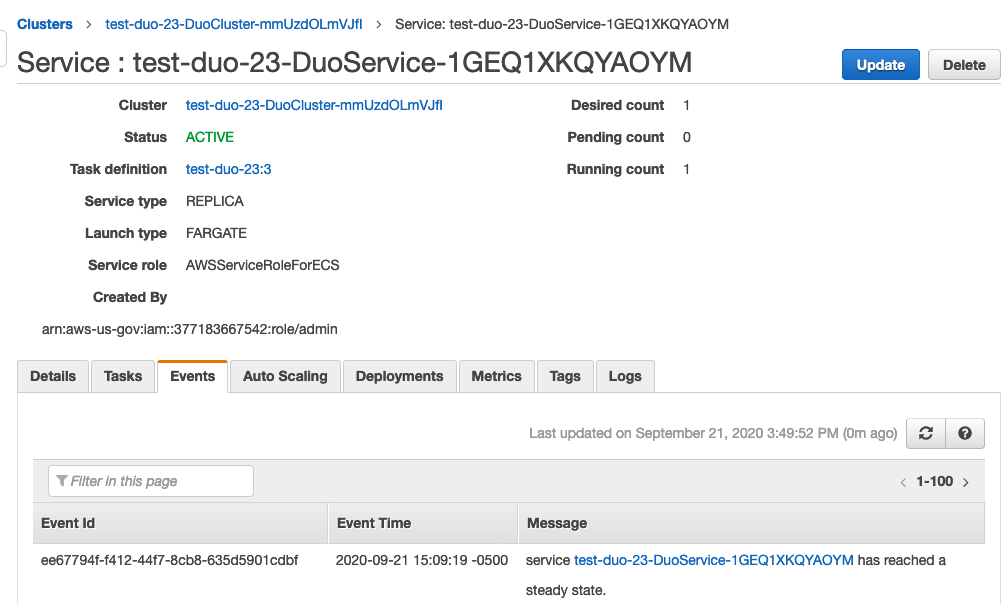
RadiusProxyServerCount, and choose the desired value. Wait until the message says that the service "has reached a steady state," as shown in Figure 2.
After each task is configured, the Amazon ECS service invokes an event that sends a notification that the service has reached a steady state, as shown in Figure 2.
Troubleshooting
For troubleshooting common Partner Solution issues, refer to the AWS Partner Solution General Information Guide and Troubleshooting CloudFormation.
If your Directory Service’s MFA status is in a Failed status, check the following:
-
Ensure that the RADIUS ECS tasks have access to the internet. This Partner Solution launches the RADIUS ECS tasks in the same subnet as the DNS servers in Directory Service. The subnet must have a route to the internet (typically through a NAT gateway) to install the Duo Authentication Proxy and other required tools used to configure Directory Service.
-
Ensure that the security group associated with the Directory Service DNS servers have a rule that allows output traffic on port 1812 to the security group created by this Partner Solution.
-
To find the security group associated with your DNS servers, open the Directory Service console, and note the IP addresses under DNS address.
-
Open the EC2 console, and choose Network Interfaces link from the menu.
-
In the search field, enter one of the DNS IP addresses you found in the previous step.
-
From the lower pane of the console, choose View outbound rules and determine whether there is a rule allowing egress on port 1812 for User Datagram Protocol (UDP) to the IP address space or security group associated with your RADIUS EC2 instances. To find the security group associated with your RADIUS EC2 instances, look up DuoRadiusProxySecurityGroup in the AWS CloudFormation stack output.
-
For advanced troubleshooting, perform the following:
-
View the Lambda function logs in CloudWatch Logs.
-
View the RADIUS proxy logs in CloudWatch Logs.
-
View the Amazon ECS task logs in CloudWatch Logs.
View the Lambda function logs in CloudWatch Logs
-
Open the AWS CloudFormation console, and select the stack that was just launched.
-
Choose the Resources tab.
-
Look for UpdateDirectoryServiceMfaSettingsCloudWatchLogsGroup in the Logical ID column and choose the resource link in the Physical ID column. This opens a CloudWatch Logs log group for the Lambda function that is responsible for configuring the MFA settings for Directory Service. You should see one or more log streams.
-
Select each one, and review any error conditions.
View the RADIUS proxy logs in CloudWatch Logs
-
Open the AWS CloudFormation console, and select the stack that was just launched.
-
Choose the Resources tab.
-
Look for RadiusProxyCloudWatchLogsGroup in the Logical ID column, and choose the resource link in the Physical ID column. This opens a CloudWatch Logs log group for the Duo Authentication Proxy running on each of the RADIUS ECS tasks. You should see one or more log streams. Each stream represents logs from the Duo Authentication Proxy on each Amazon ECS task.
-
Select each log stream, and look for error messages. If there aren’t any log streams in the log group, the instances might not have access to the internet.
View the Amazon ECS task logs in CloudWatch Logs
-
Look for ECS Cluster. Under ECS service, you should see two tasks with a status of Pending or Running.
-
Choose one of the tasks, and view the logs in CloudWatch using either of these methods.
-
Choose the top tab (Logs).
-
In the Containers section, choose View logs in CloudWatch.
FAQ
Q. Fargate containers fail with the error ResourceInitializationError: unable to pull secrets or registry auth: execution resource retrieval failed: unable to retrieve secret from asm: service call has been retried 1 time(s): failed to fetch secret.
A. This error occurs if a Directory Service subnet is not private on a NAT. The Fargate subnets are same as the Directory Service subnets. Change the template to allow networking for Fargate tasks. See Fargate task networking.
Customer responsibility
After you deploy a Partner Solution, confirm that your resources and services are updated and configured—including any required patches—to meet your security and other needs. For more information, refer to the Shared Responsibility Model.
Feedback
To submit feature ideas and report bugs, use the Issues section of the GitHub repository for this Partner Solution. To submit code, refer to the Partner Solution Contributor’s Guide. To submit feedback on this deployment guide, use the following GitHub links:
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS products or services, each of which is provided "as is" without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at https://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "as is" basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.