IBM Cloud Pak for Security on AWS
Partner Solution Deployment Guide

March 2022
Ann Hayes, Patrick Kent Dacoliat, Kieran O Mahony, Manoj Nanjala, Divya Dinesan, Bhavana R, Samrika Singh, and Shinu Shaju, IBM
Vinod Shukla, AWS Integration & Automation team

| Refer to the GitHub repository to view source files, report bugs, submit feature ideas, and post feedback about this Partner Solution. To comment on the documentation, refer to Feedback. |
This Partner Solution was created by IBM in collaboration with Amazon Web Services (AWS). Partner Solutions are automated reference deployments that help people deploy popular technologies on AWS according to AWS best practices. If you’re unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Overview
This Partner Solution deploys IBM Cloud Pak for Security on the AWS Cloud. If you are unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
IBM Cloud Pak for Security can connect disparate data sources - to uncover hidden threats and make better risk-based decisions - while the data stays where it is. By using open standards and IBM innovations, IBM Cloud Pak for Security can securely access IBM and third-party tools to search for threat indicators across any cloud or on-premises location. Connect your workflows with a unified interface so you can respond faster to security incidents. Use IBM Cloud Pak for Security to orchestrate and automate your security response so that you can better prioritize your team’s time.
IBM Cloud Pak for Security deploys the following applications:
-
IBM® Security Data Explorer is a new application that enables customers to do federated search and investigation across their hybrid, multi-cloud environment in a single interface and workflow.
-
Threat Intelligence Insights is an application that delivers unique, actionable, and timely threat intelligence.
-
IBM® Security QRadar SOAR for IBM Cloud Pak for Security provides organizations with the ability to track, manage, and resolve cybersecurity incidents.
-
IBM® Security Risk Manager for IBM Cloud Pak for Security is an application that automatically collects, correlates, and contextualizes risk insights across the IT and security ecosystem of your organization.
-
IBM® Security Threat Investigator automatically analyzes and investigates cases to help you make more informed decisions. By showing potential threats and the assets that are impacted, Threat Investigator can help determine the criticality of exposure, how many systems are at risk, and the level of remediation effort that is required.
-
IBM® Detection and Response Center (Beta) provides an overview of your organization’s security posture through the security use cases available from IBM QRadar and the Sigma community tools. IBM Security Threat Investigator uses these security use cases in its investigations.
For more information on IBM Cloud Pak for Security, see the IBM Cloud Pak for Security Documentation.
Costs and licenses
There is no cost to use this Partner Solution, but you will be billed for any AWS services or resources that this Partner Solution deploys. For more information, refer to the AWS Partner Solution General Information Guide.
For IBM Cloud Pak for Security product and pricing information, or to use your existing entitlements, contact your IBM sales representative at +1 (877) 426-3774 or online at IBM Cloud Pak for Security. For more information about licensing terms, see the IBM Cloud Pak for Security software license agreement.
Depending on your purchase of IBM Cloud Pak for Security, you can additionally choose to install the Orchestration & Automation application on IBM Cloud Pak for Security platform, you must accquire a license key to access its capabilities in conjunction with IBM Cloud Pak for Security license. For more information on the Orchestration & Automation license, see the IBM Cloud Pak for Security documentation on Licensing and Entitlement.
Architecture
Deploying this Partner Solution with default parameters builds the following IBM Cloud Pak for Security environment in the AWS Cloud.
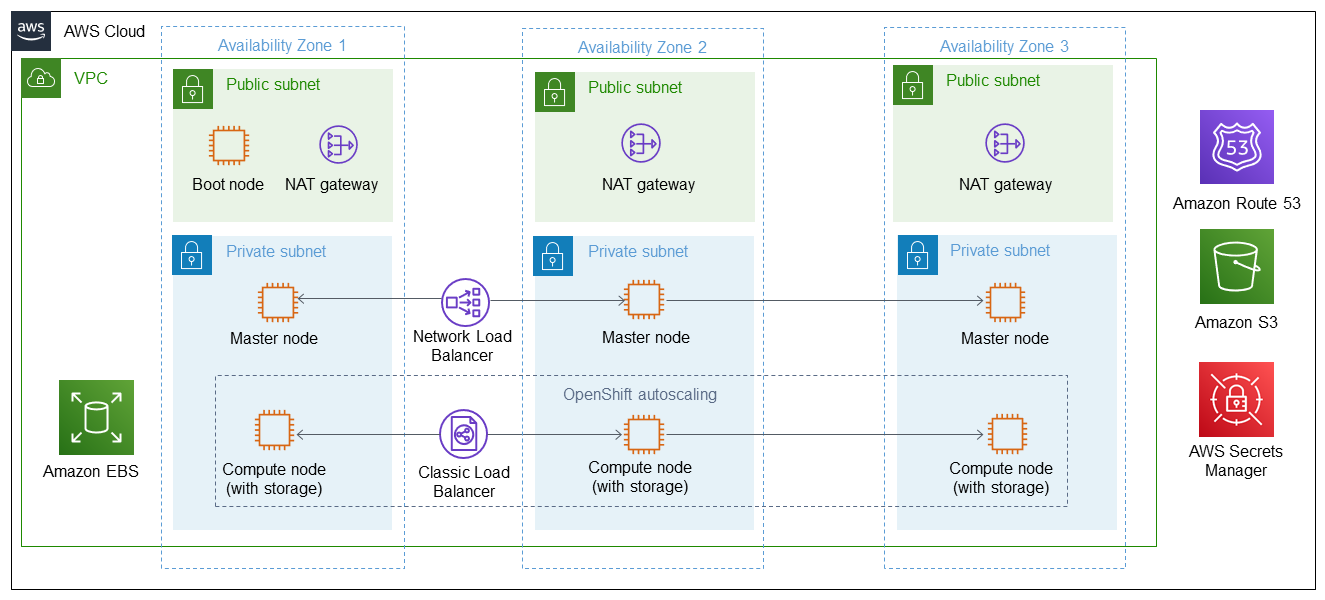
As shown in Figure 1, this Partner Solution sets up the following:
-
A highly available architecture that spans across three Availability Zones.*
-
A virtual private cloud (VPC) configured with public and private subnets, according to AWS best practices, to provide you with your own virtual network on AWS.*
-
In the public subnets:
-
Managed network address translation (NAT) gateways to allow outbound internet access for resources in the private subnets.*
-
A boot node Amazon EC2 instance that also serves as a bastion host to allow inbound Secure Shell (SSH) access to EC2 instances in the private subnets.
-
-
In the private subnets:
-
Red Hat OpenShift Container Platform (OCP) master nodes in up to three Availability Zones.
-
OCP compute nodes with OpenShift autoscaling for hosting the IBM Cloud Pak for Security capabilities. Amazon EBS disks are mounted on the compute nodes for container-persistent data.
-
-
A Classic Load Balancer spanning the public subnets for accessing IBM Cloud Pak for Security from a web browser.
-
A Network Load Balancer spanning the public subnets for routing external OpenShift application programming interface (API) traffic to the OCP master instances.
-
A Network Load Balancer spanning the private subnets for routing internal OpenShift API traffic to the OCP master instances.
-
OpenShift autoscaling for the OCP compute nodes.
-
Amazon Route 53 as your public Domain Name System (DNS) for resolving domain names of the IBM Cloud Pak for Security management console and applications deployed on the cluster.
-
Amazon Simple Storage Service (Amazon S3) for storing the pull secret, TLS certificate and key, SOAR Entitlement and OpenShift image registry.
-
AWS Secrets Manager to encrypt, store, and retrieve credentials and secrets for your IBM Cloud Pak for Security deployment.
The IBM Cloud Pak for Security components run as containers on the OpenShift compute nodes, and build on a range of common platform and operational services that underpin all IBM Cloud Paks.
* The template that deploys this Partner Solution into an existing VPC skips the components marked by asterisks and prompts you for your existing VPC configuration.
Deployment options
This Partner Solution provides the following deployment options:
-
Deploy IBM Cloud Pak for Security into a new VPC. This option builds a new AWS environment that consists of the VPC, subnets, NAT gateways, security groups, bastion hosts, and other infrastructure components. It then deploys IBM Cloud Pak for Security into this new VPC.
-
Deploy IBM Cloud Pak for Security into an existing VPC. This option provisions IBM Cloud Pak for Security in your existing AWS infrastructure.
This Partner Solution provides separate templates for these options. It also lets you configure Classless Inter-Domain Routing (CIDR) blocks, instance types, and IBM Cloud Pak for Security settings.
Predeployment steps
Create an Amazon Simple Storage Service (Amazon S3) bucket
You need to create an S3 bucket in one of the AWS Regions. See AWS documentation on how to Create your first S3 bucket.
To upload files into your S3 bucket, see Upload an object to your bucket.
This S3 bucket is used for storing Red Hat OpenShift pull secret which is required for deploying IBM Cloud Pak for Security. Additionally, it can also be used to store the optional TLS certificates, keys, and SOAR Entitlement.
Sign up for a Red Hat subscription
This Partner Solution requires a Red Hat subscription. During the deployment of the Partner Solution, provide your OpenShift Installer Provisioned Infrastructure pull secret.
If you don’t have a Red Hat account, you can create one on the Red Hat website. Note that registration may require a non-personal email address. To get a 60-day evaluation license for OpenShift, see the instructions in Red Hat OpenShift Container Platform.
Upload the OpenShift pull secret to your S3 bucket. The Partner Solution pulls this secret from your S3 bucket location to provision the cluster.
IBM Cloud Pak for Security subscription
-
The Partner Solution requires an entitlement key to access the IBM Cloud Pak for Security content.
-
You can acquire your IBM entitlement key from IBM Container Library.
-
During stack creation you will need to pass the IBM entitlement key as the
RepositoryPasswordparameter.
-
-
The Partner Solution uses an optional
SOAR Entitlementfor Orchestration & Automation application on IBM Cloud Pak for Security.-
To know how to acquire your SOAR Entitlement, see the IBM Cloud Pak for Security documentation on Licensing and Entitlement.
-
Upload the SOAR Entitlement to your S3 bucket. The Partner Solution pulls this SOAR Entitlement from the specified S3 bucket location for configuring Orchestration & Automation.
-
Domain name and TLS certificates
Confirm that you have a domain name to use for OpenShift in Amazon Route 53. If you do not have a domain name, see the AWS documentation on Registering a new domain.
IBM Cloud Pak for Security can be installed using the FQDN and TLS certificates of the Red Hat® OpenShift® Container Platform by not passing in an FQDN in the optional CP4SFQDN parameter during installation. If you choose this method, you don’t have to create your own fully qualified domain name.
|
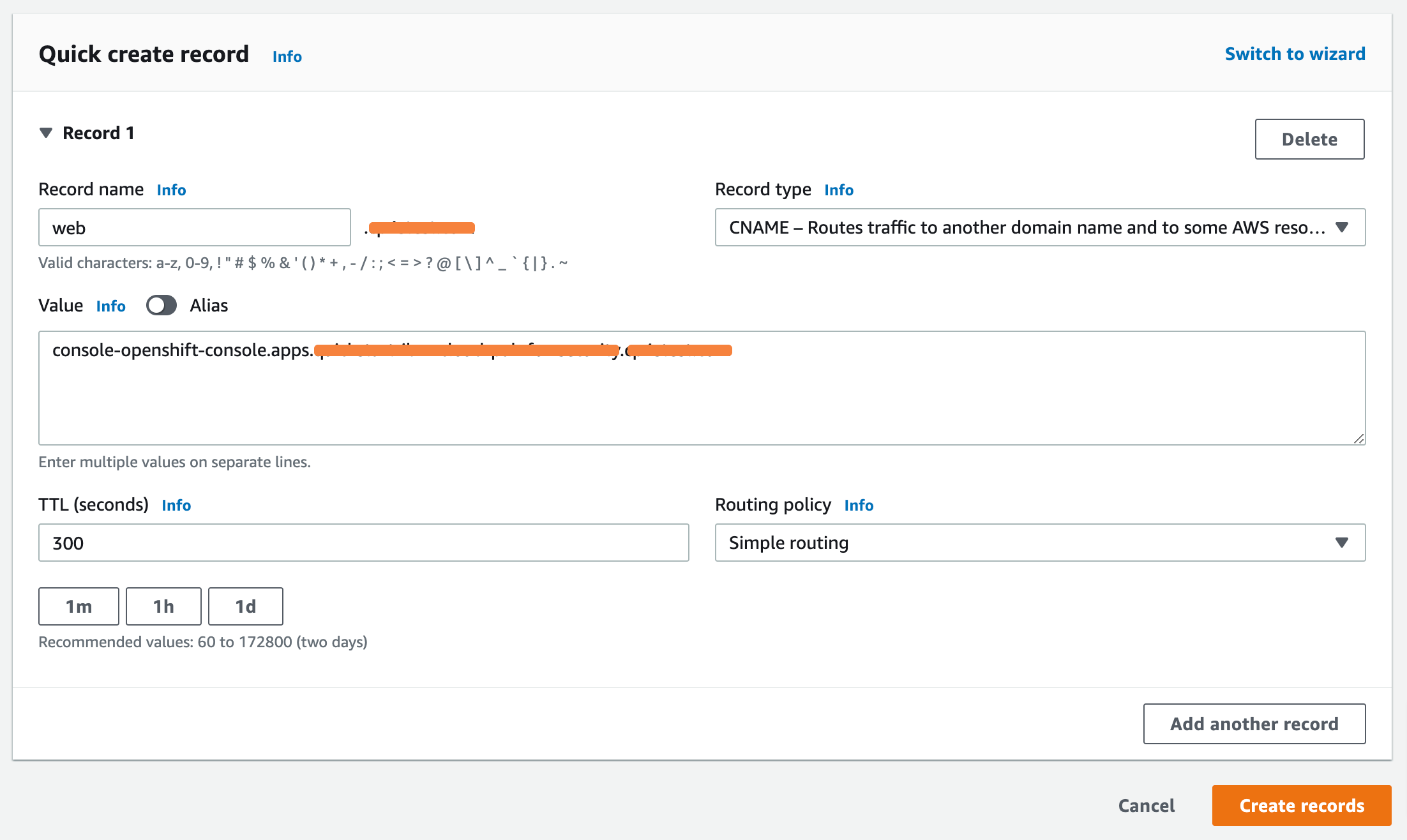
If you wish to create your own FQDN for the IBM Cloud Pak for Security, add a DNS record to your hosted zone in Amazon Route 53.
The following procedure explains how to create records using the Amazon Route 53 console.
-
Go to Amazon Route 53 console. Click here.
-
Choose the hosted zone that corresponds to the domain name you will use when creating the stack.
-
Choose Create Record.
-
Enter a value for record name, this record will be used for the IBM Cloud Pak for Security
CP4SFQDNparameter value when creating the stack.Make sure that your FQDN must not be the same as the Red Hat OpenShift Container Platform cluster FQDN, or any other FQDN associated with the Red Hat OpenShift Container Platform cluster. -
Confirm that the record type is
CNAME. -
For the value of the record, specify
console-openshift-console.apps.ClusterName.DomainName, whereClusterNameandDomainNameare the respective input parameters used when creating the stack. -
For the routing policy, pick
Simple routing, and then choose Create record, as shown in Figure 2.
If you are using your own FQDN, you must provide an optional TLS certificate and TLS key, that use keys that are signed by a trusted certificate authority (CA). A custom TLS certificate is required, if the provided server keys are not signed by a trusted certificate authority. For more information, see the IBM Cloud Pak for Security documentation on Domain Name and TLS Certificates.
Upload the TLS certificate, TLS key and custom TLS certificate to your S3 bucket. The Partner Solution pulls these certificates and keys from your S3 bucket location for IBM Cloud Pak for Security deployment.
Deployment steps
-
Sign in to your AWS account, and launch this Partner Solution, as described under Deployment options. The AWS CloudFormation console opens with a prepopulated template.
-
Choose the correct AWS Region, and then choose Next.
-
On the Create stack page, keep the default setting for the template URL, and then choose Next.
-
On the Specify stack details page, change the stack name if needed. Review the parameters for the template. Provide values for the parameters that require input. For all other parameters, review the default settings and customize them as necessary. When you finish reviewing and customizing the parameters, choose Next.
Unless you’re customizing the Partner Solution templates or are instructed otherwise in this guide’s Predeployment section, don’t change the default settings for the following parameters: QSS3BucketName,QSS3BucketRegion, andQSS3KeyPrefix. Changing the values of these parameters will modify code references that point to the Amazon Simple Storage Service (Amazon S3) bucket name and key prefix. For more information, refer to the AWS Partner Solutions Contributor’s Guide. -
On the Configure stack options page, you can specify tags (key-value pairs) for resources in your stack and set advanced options. When you finish, choose Next.
-
On the Review page, review and confirm the template settings. Under Capabilities, select all of the check boxes to acknowledge that the template creates AWS Identity and Access Management (IAM) resources that might require the ability to automatically expand macros.
-
Choose Create stack. The stack takes about 2 hours to deploy.
-
Monitor the stack’s status, and when the status is CREATE_COMPLETE, the IBM Cloud Pak for Security deployment is ready.
-
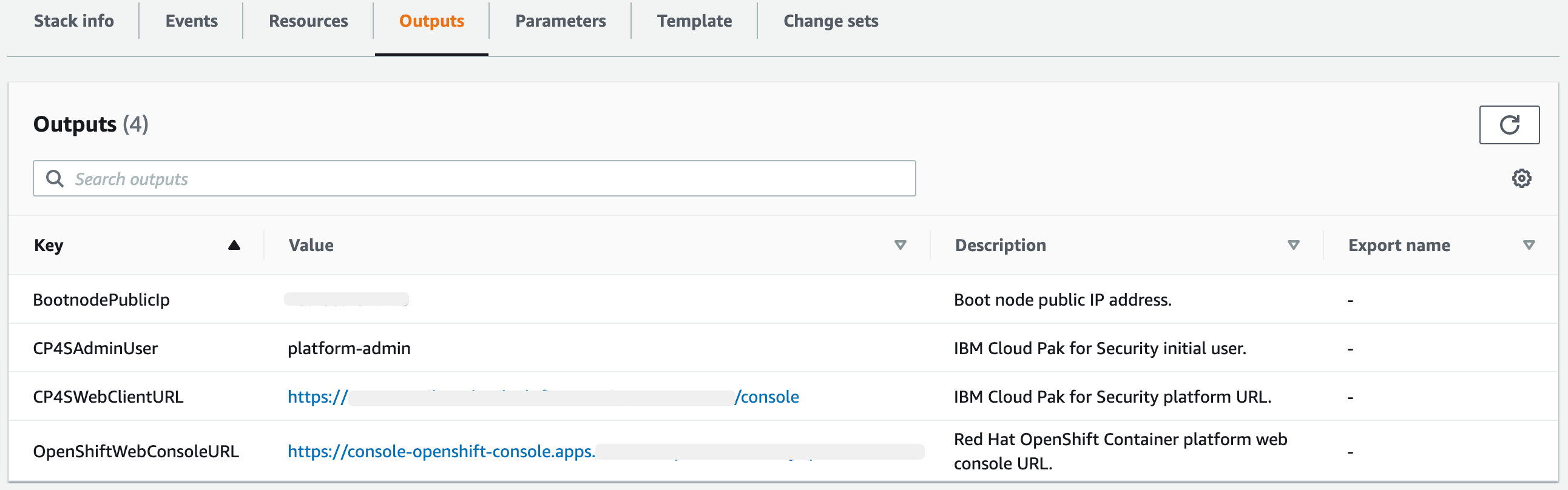
To view the created resources, choose the Outputs tab.
Postdeployment steps
Configuring Identity Provider authentication
To log in to IBM Cloud Pak for Security, you must configure at least one Identity Provider (IDP). The CP4SAdminUser, shown in Figure 3, that you provided while creating the stack must exist in the choosen Identity Provider (IDP). This CP4SAdminUser is the initial user who can log in and add other users. Use the password that you specified for the user when you configured the Identity Provider (IDP). To know more details on configuring Identity Provider (IDP) authentication, see the IBM Cloud Pak for Security documentation on Configuring Identity Provider Authentication.
Login into IBM Cloud Pak for Security as the initial user
After configuring at least one Identity Provider (IDP) navigate to the CP4SWebClientURL output of the root stack, shown in Figure 3.
Log in to the IBM Cloud Pak for Security web client by choosing Enterprise LDAP authentication, and then enter the CP4SAdminUser value and the admin password that you supplied while configuring LDAP authentication during post installation.
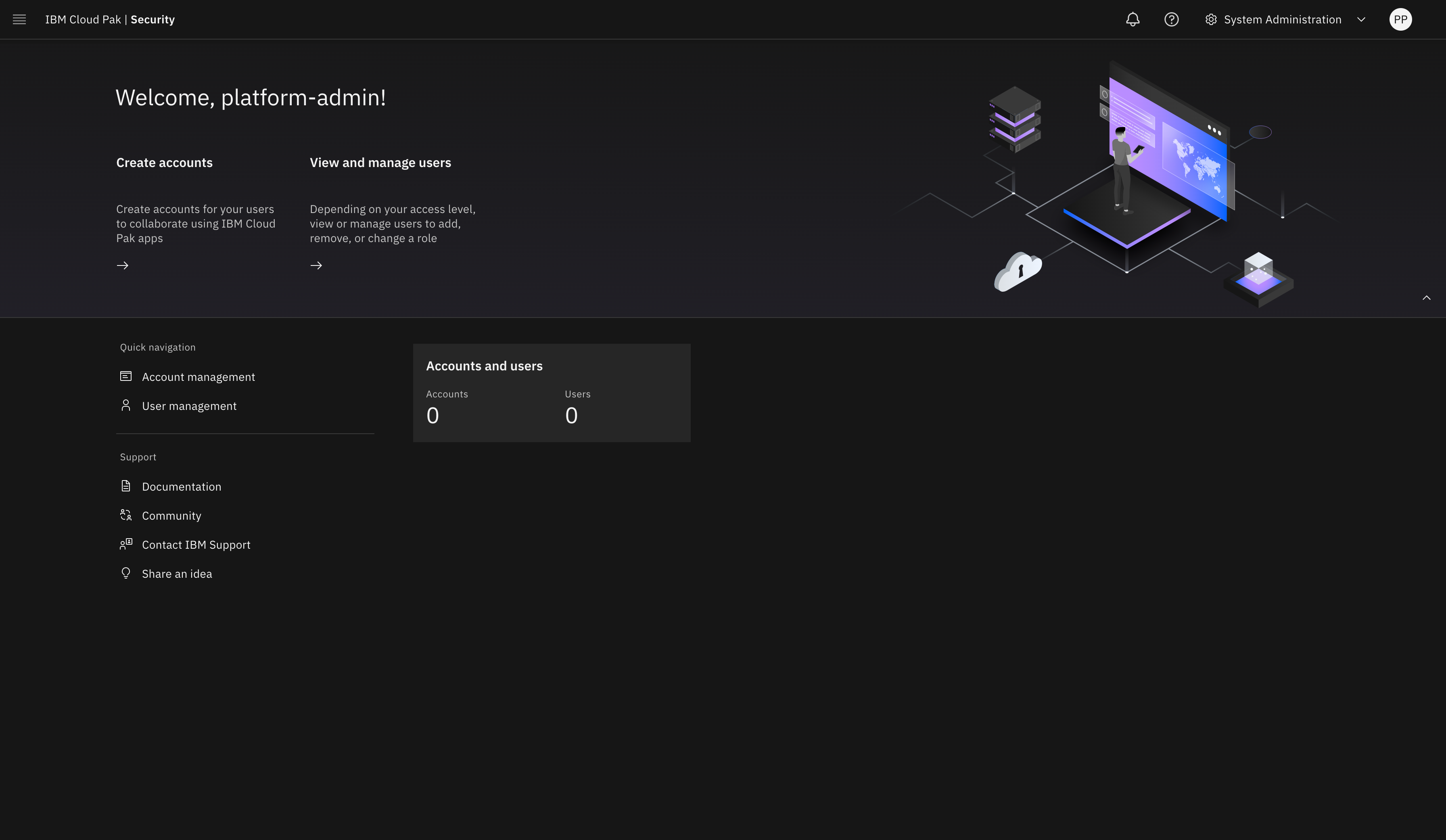
Upon logging in to the IBM Cloud Pak for Security web client URL, the welcome page opens for the System Administrator account, as shown in Figure 5.
Create accounts in IBM Cloud Pak for Security
As a system administrator, you can create Standard or Provider accounts in IBM Cloud Pak for Security, or delete existing accounts. You must be working in the System Administration account and have the required permission to manage accounts. For more details, see the IBM Cloud Pak for Security documentation on Creating or Deleting Accounts.
Configure a data source connection
To begin working with applications, enable IBM Cloud Pak for Security to connect with data sources. For more details, see the IBM Cloud Pak for Security documentation on Configuring a Data Source Connection.
Manage your cluster using the Red Hat OpenShift web console
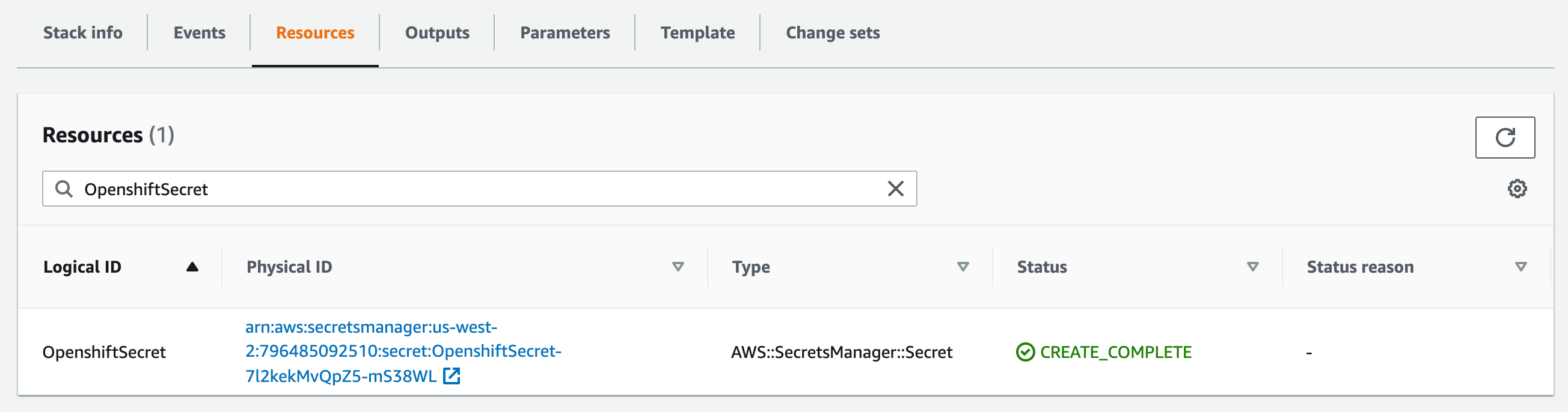
To access the Red Hat Openshift Container Platform web console, navigate to the OpenshiftWebConsoleURL in the Outputs tab of the root stack. See, Figure 3.
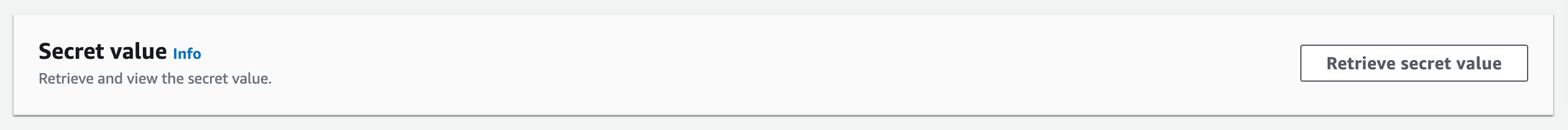
Log in to the Openshift web console by using use the default OpenShift administrator kubeadmin. The password can be obtained from the OpenShiftSecret resource from the Resources tab of IBM Cloud Pak for Security stack.
You can retrieve the secret value by choosing Retrieve secret value, as shown in the following figure. Use this secret value as OpenShift console administrative password.
Accessing Red Hat OpenShift cluster from the command-line interface
-
In your Red Hat OpenShift web console, choose your profile name and then select Copy Login.
-
Choose Display Token, copy the oc login command, and paste the command into your command line.
Troubleshooting
Make notes of the the log files that are generated in the output S3 bucket:
-
bootstrap.log - STDOUT of the high overview of the events during deployment of Red Hat OpenShift Container Platform and IBM Cloud Pak for Security.
-
ocp_install.log - STDOUT of the deployment of Red Hat OpenShift Container Platform using IPI.
-
cp4s_install.log - STDOUT of the deployment of IBM Cloud Pak for Security including the validation of the installation and deployment of SOAR Entitlement.
For troubleshooting IBM Cloud Pak for Security related issues, refer to the IBM Cloud Pak for Security Troubleshooting and Support Guide.
For troubleshooting common Partner Solution issues, refer to the AWS Partner Solution General Information Guide and Troubleshooting CloudFormation.
Customer responsibility
After you deploy a Partner Solution, confirm that your resources and services are updated and configured—including any required patches—to meet your security and other needs. For more information, refer to the Shared Responsibility Model.
Feedback
To submit feature ideas and report bugs, use the Issues section of the GitHub repository for this Partner Solution. To submit code, refer to the Partner Solution Contributor’s Guide. To submit feedback on this deployment guide, use the following GitHub links:
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS products or services, each of which is provided "as is" without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at https://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "as is" basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.