Windows Server Update Services on AWS
Partner Solution Deployment Guide

December 2023
Sepehr Samiei and Dave May, AWS

| Refer to the GitHub repository to view source files, report bugs, submit feature ideas, and post feedback about this Partner Solution. To comment on the documentation, refer to Feedback. |
This Partner Solution was created by Amazon Web Services (AWS). Partner Solutions are automated reference deployments that help people deploy popular technologies on AWS according to AWS best practices. If you’re unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Overview
This guide covers the information you need to deploy the Windows Server Update Services Partner Solution in the AWS Cloud.
WSUS
WSUS is a server role included with Windows Server at no additional cost. It can perform the following functions:
-
Download required updates and patches from the internet and act as an internally managed proxy server.
-
Manage clients, including other Windows servers, by defining policies that approve or decline updates and patches, and report compliance status of clients.
Windows operating systems can directly acquire Microsoft updates from the internet, or they can be configured to acquire updates from a WSUS endpoint. AWS customers can deploy WSUS as a centralized Microsoft update repository.
WSUS on AWS
This solution deploys a WSUS endpoint for downloading updates. Client and policy management can be performed by AWS Systems Manager or by the traditional WSUS console with Microsoft Active Directory Group Policy.
Conventionally, system administrators often rely on Active Directory Group Policy or Microsoft System Center Configuration Manager (SCCM) to manage WSUS clients. This requires servers and workstations to be Active Directory domain-joined and can include the complexity and cost of using SCCM.
This solution is designed to use Systems Manager for deployment, configuration, management, and consumption of WSUS. This includes both Active Directory domain-joined and standalone Windows clients.
Costs and licenses
There is no cost to use this Partner Solution, but you will be billed for any AWS services or resources that this Partner Solution deploys. For more information, refer to the AWS Partner Solution General Information Guide.
By default, this solution deploys WSUS on a single Windows instance, using a license-included Amazon Machine Image (AMI). Windows licensing cost is paid through a Service Provider Licensing Agreement (SPLA) and is included in your monthly AWS bill. You can optionally choose to use Microsoft SQL Server Standard Edition for the WSUS database. In this case, WSUS is deployed on a single Windows instance, using the license-included SQL Server Standard on Windows AMI. All licensing costs are added to your monthly AWS bill.
Architecture
Deploying this Partner Solution with default parameters builds the following WSUS environment in the AWS Cloud.
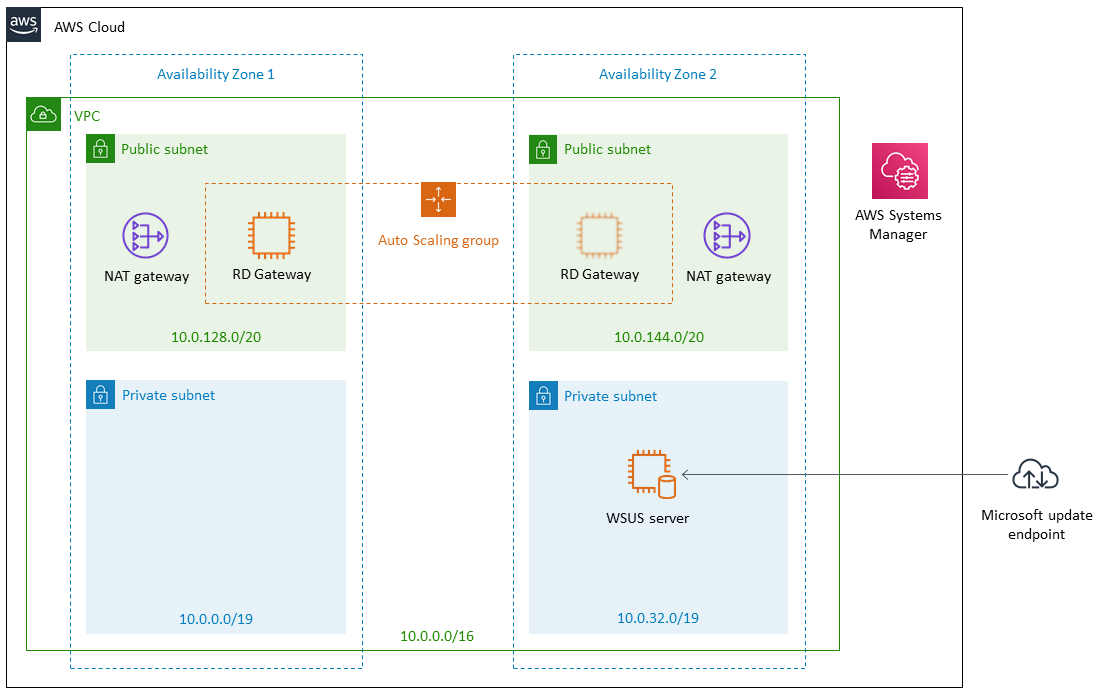
As shown in Figure 1, this Partner Solution sets up the following:
-
A VPC configured with public and private subnets according to AWS best practices, to provide you with your own virtual network on AWS.*
-
In the public subnets, managed network address translation (NAT) gateways to allow outbound internet access for resources in the private subnets.*
-
In the private subnet, a Windows instance with the WSUS role configured on it. WSUS can then be managed by using either Systems Manager Automation or the traditional WSUS console.
-
Optionally, a Remote Desktop Gateway (RD Gateway) in an Auto Scaling group in the public subnets for remote access to the WSUS instance.
* The template that deploys this Partner Solution into an existing VPC skips the components marked by asterisks and prompts you for your existing VPC configuration.
Deployment options
This Partner Solution provides the following deployment options:
-
Deploy WSUS into a new VPC. This option builds a new AWS environment that consists of the VPC, subnets, NAT gateways, security groups, bastion hosts, and other infrastructure components. It then deploys WSUS into this new VPC.
-
Deploy WSUS into an existing VPC. This option provisions WSUS in your existing AWS infrastructure.
This Partner Solution provides separate templates for these options. It also lets you configure Classless Inter-Domain Routing (CIDR) blocks, instance types, and WSUS settings.
Deployment steps
-
Sign in to your AWS account, and launch this Partner Solution, as described under Deployment options. The AWS CloudFormation console opens with a prepopulated template.
-
Choose the correct AWS Region, and then choose Next.
-
On the Create stack page, keep the default setting for the template URL, and then choose Next.
-
On the Specify stack details page, change the stack name if needed. Review the parameters for the template. Provide values for the parameters that require input. For all other parameters, review the default settings and customize them as necessary. When you finish reviewing and customizing the parameters, choose Next.
Unless you’re customizing the Partner Solution templates or are instructed otherwise in this guide’s Predeployment section, don’t change the default settings for the following parameters: QSS3BucketName,QSS3BucketRegion, andQSS3KeyPrefix. Changing the values of these parameters will modify code references that point to the Amazon Simple Storage Service (Amazon S3) bucket name and key prefix. For more information, refer to the AWS Partner Solutions Contributor’s Guide. -
On the Configure stack options page, you can specify tags (key-value pairs) for resources in your stack and set advanced options. When you finish, choose Next.
-
On the Review page, review and confirm the template settings. Under Capabilities, select all of the check boxes to acknowledge that the template creates AWS Identity and Access Management (IAM) resources that might require the ability to automatically expand macros.
-
Choose Create stack. The stack takes about 30 minutes to deploy.
-
Monitor the stack’s status, and when the status is CREATE_COMPLETE, the Windows Server Update Services deployment is ready.
-
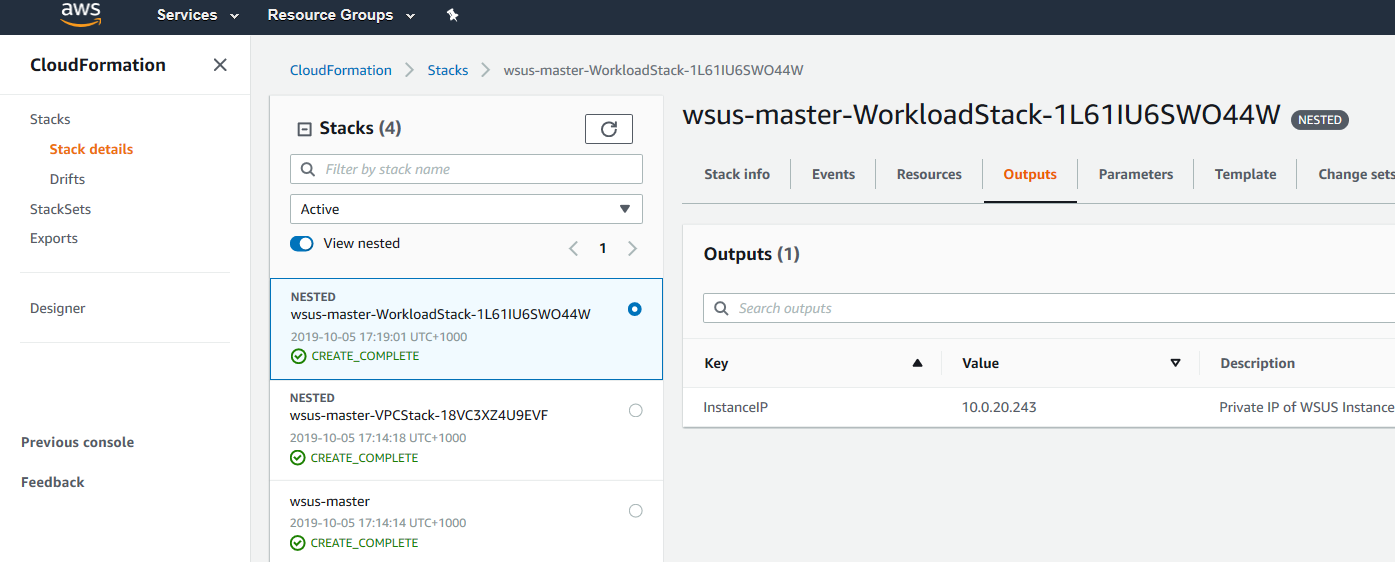
To view the created resources, choose the Outputs tab.
Postdeployment steps
Test the deployment
Once the CloudFormation stack creation is completed, your WSUS instance is deployed and configured. To test or use it, perform the following steps:
-
Approve or deny updates and patches for target computer groups.
-
Wait until WSUS synchronization completes, and all approved updates are downloaded.
-
Point other servers and workstations to your WSUS instance as the update point.
-
Trigger updates on WSUS clients.
You can perform these steps in multiple ways. The next section describes best practices for performing these steps on AWS.
Best practices for testing and using WSUS on AWS
Systems Manager helps you to enhance operations on the WSUS server and also its clients.
Approve or deny updates and patches
To securely approve or deny updates on the WSUS server, or to perform other server-side operations, use AWS Systems Manager Run Command or AWS Systems Manager Session Manager. Run Command enables you to securely run Windows PowerShell cmdlets or scripts on target servers. Session Manager allows you to do the same thing using an interactive session.
A sample PowerShell script is included in the GitHub repository for this Quick Start. You can modify this script and run it on your WSUS instance by using Systems Manager Run Command or Session Manager. If you deployed this WSUS Quick Start with the optional RD Gateway Auto Scaling group, you can use Remote Desktop Protocol (RDP) to connect from the RD Gateway to the WSUS server and use the traditional WSUS console. If you did not deploy the Quick Start with the RD Gateway Auto Scaling group, you can use the Session Manager Port Forwarding document to establish an RDP session directly to the WSUS server.
Point other servers and workstations to your WSUS instance
To configure WSUS clients to use the WSUS endpoint, use AWS Systems Manager State Manager or Run Command. For both standalone and domain-joined Windows instances, you can use Set-ClientWSUSSetting.ps1 for this purpose (in this case, the easiest way is to remove the first and last lines to convert the function into a script file).
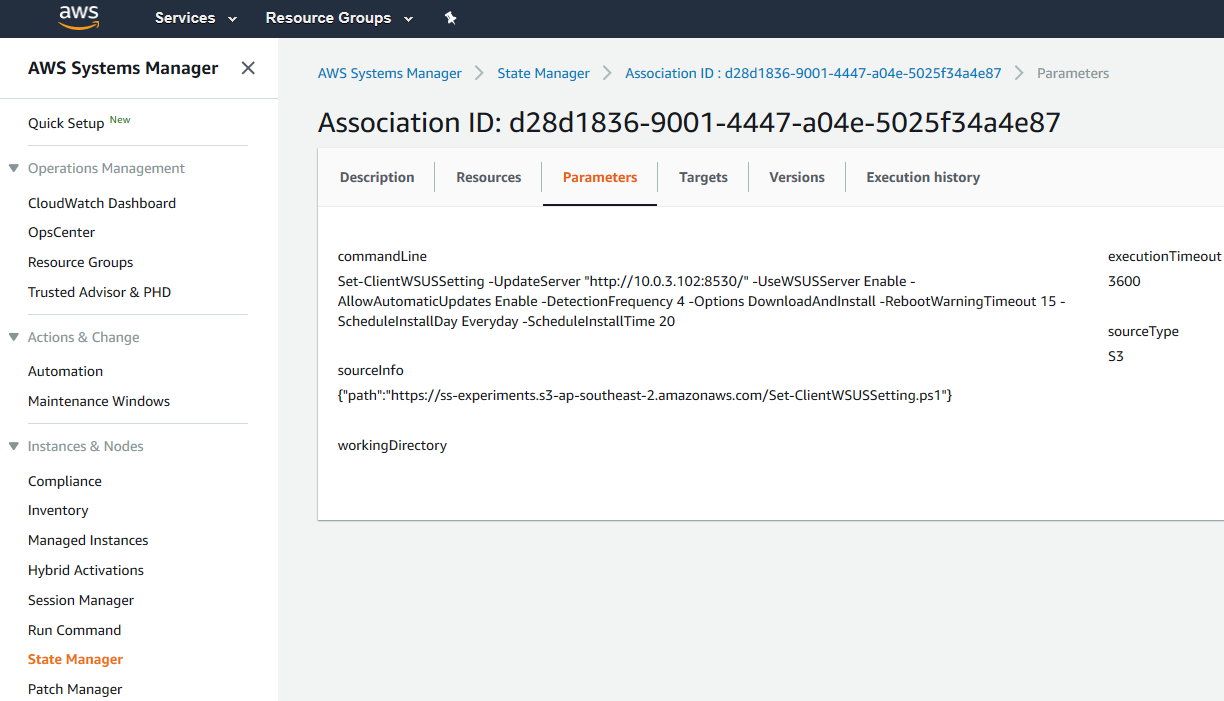
Figure 3: Using State Manager to configure WSUS clients
For domain-joined Windows instances, you can also use Group Policy Objects (GPO) to configure WSUS client settings.
Trigger updates on WSUS clients
To define patch baselines, use AWS Systems Manager Patch Manager. To regularly and automatically trigger updates on WSUS clients, use AWS Systems Manager Maintenance Windows to schedule Run Command or State Manager tasks.
Troubleshooting
For troubleshooting common Partner Solution issues, refer to the AWS Partner Solution General Information Guide and Troubleshooting CloudFormation.
Customer responsibility
After you deploy a Partner Solution, confirm that your resources and services are updated and configured—including any required patches—to meet your security and other needs. For more information, refer to the Shared Responsibility Model.
Feedback
To submit feature ideas and report bugs, use the Issues section of the GitHub repository for this Partner Solution. To submit code, refer to the Partner Solution Contributor’s Guide. To submit feedback on this deployment guide, use the following GitHub links:
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS products or services, each of which is provided "as is" without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at https://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "as is" basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.