Sumo Logic Security Integrations for AWS Organizations on AWS
Partner Solution Deployment Guide

June 2022
Arun Patyal and Himanshu Pal, Sumo Logic
Dilip Rajan, Suresh Veeragoni, and Vinay Maddi, AWS Data & Analytics Partner SA team

This Partner Solution was created by Sumo Logic in collaboration with Amazon Web Services (AWS). Partner Solutions are automated reference deployments that help people deploy popular technologies on AWS according to AWS best practices. If you’re unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Overview
This Quick Start deploys Sumo Logic Security Integrations for AWS Organizations on the AWS Cloud. It’s for DevOps and IT operations that want to provide Sumo Logic security analytics across multiple AWS accounts. If you are unfamiliar with AWS Quick Starts, refer to the AWS Quick Start General Information Guide.
Deploying this Quick Start does not guarantee an organization’s compliance with any laws, certifications, policies, or other regulations.
Costs and licenses
Sumo Logic provides a free tier with unlimited queries and 30-day free trials for various licensing options. For more information, refer to the Sumo Logic website.
Architecture
Deploying this Quick Start with default parameters builds the following architecture.
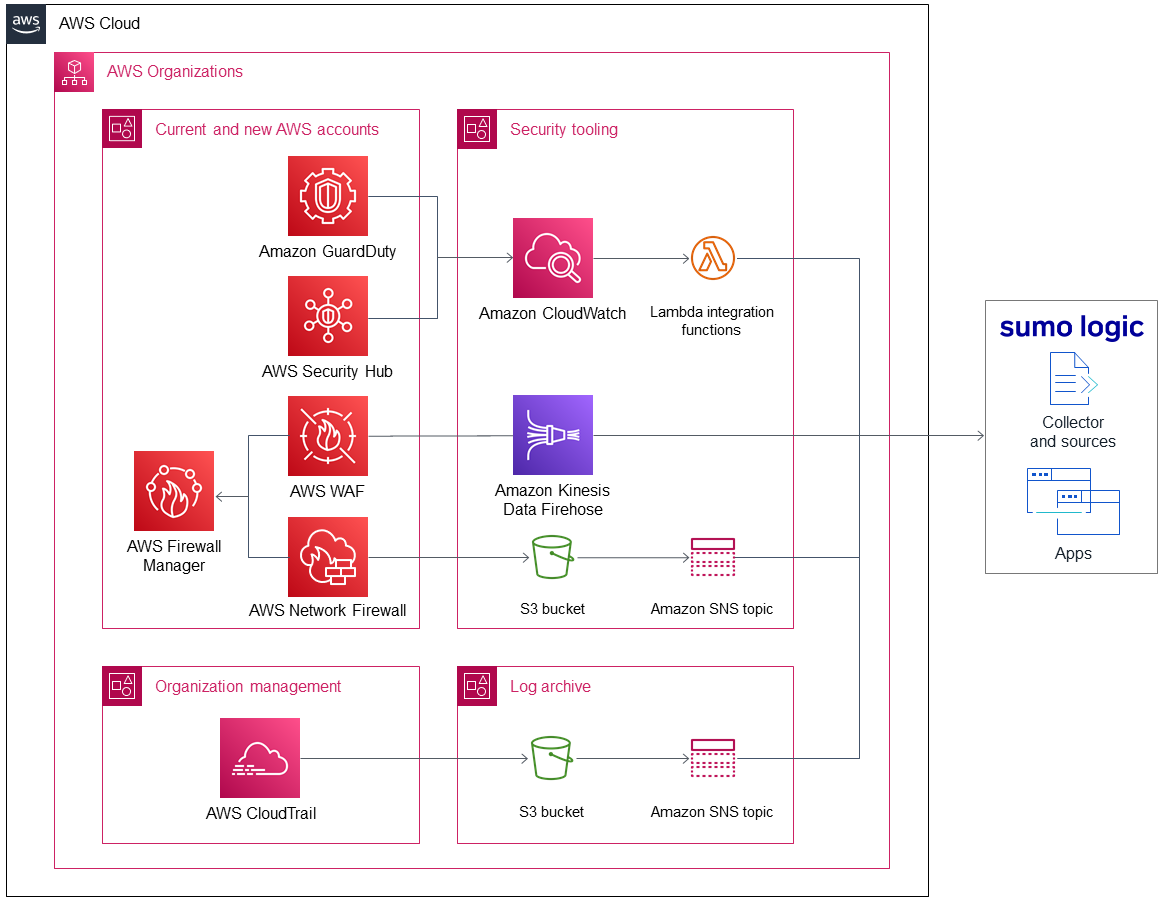
As shown in Figure 1, the Quick Start sets up the following:
-
In all current and new AWS accounts in your AWS organization:
-
Amazon GuardDuty to help protect AWS accounts and workloads from malicious activity and report security events to Amazon CloudWatch.
-
AWS Security Hub to assess security alerts and security posture across AWS accounts. Security Hub relays security events to CloudWatch.
-
AWS WAF for a web application firewall to help protect the resources in your organization from common web exploits.
-
AWS Network Firewall to deploy essential network protections for all your Amazon virtual private clouds (VPCs).
-
AWS Firewall Manager to deploy AWS WAF and AWS Network Firewall rules across the VPCs in your organization, to control traffic leaving and entering your network.
-
-
In your security tooling account:
-
Amazon CloudWatch to relay security events to AWS Lambda integration functions.
-
Lambda integration functions to do two things. First, to create a Sumo collector and multiple sources. A collector is an agent that receives logs from a source before encrypting and forwarding them to a Sumo service. A source is a configuration that collects logs from your AWS services. Second, to install the security apps you select during deployment to your Sumo logic account.
-
Amazon Kinesis Data Firehose to forward AWS WAF logs to Sumo Logic.
-
An Amazon Simple Storage Service (Amazon S3) bucket to store AWS Network Firewall logs.
-
An Amazon Simple Notification Service (Amazon SNS) topic to publish logs to Sumo Logic when Network Firewall saves logs to the S3 bucket.
-
-
In your organization management account, AWS CloudTrail to track user activity and API usage in the organization.
-
In your log archive account:
-
An Amazon Simple Storage Service (Amazon S3) bucket to store CloudTrail logs.
-
An Amazon Simple Notification Service (Amazon SNS) topic to publish logs to Sumo Logic when CloudTrail saves logs to the S3 bucket.
-
| This Quick Start deploys Amazon GuardDuty and AWS CloudTrail across all accounts in your organization, incurring costs for these services in each account. |
Deployment options
This Quick Start provides one deployment option:
This option builds new AWS environment that consists of the infrastructure resources required to provision applications to your Sumo Logic account and the necessary resources to your AWS account. During the deployment, you can choose which applications to install.
Scenarios supported by this Quick Start
This Quick Start supports the following scenarios:
-
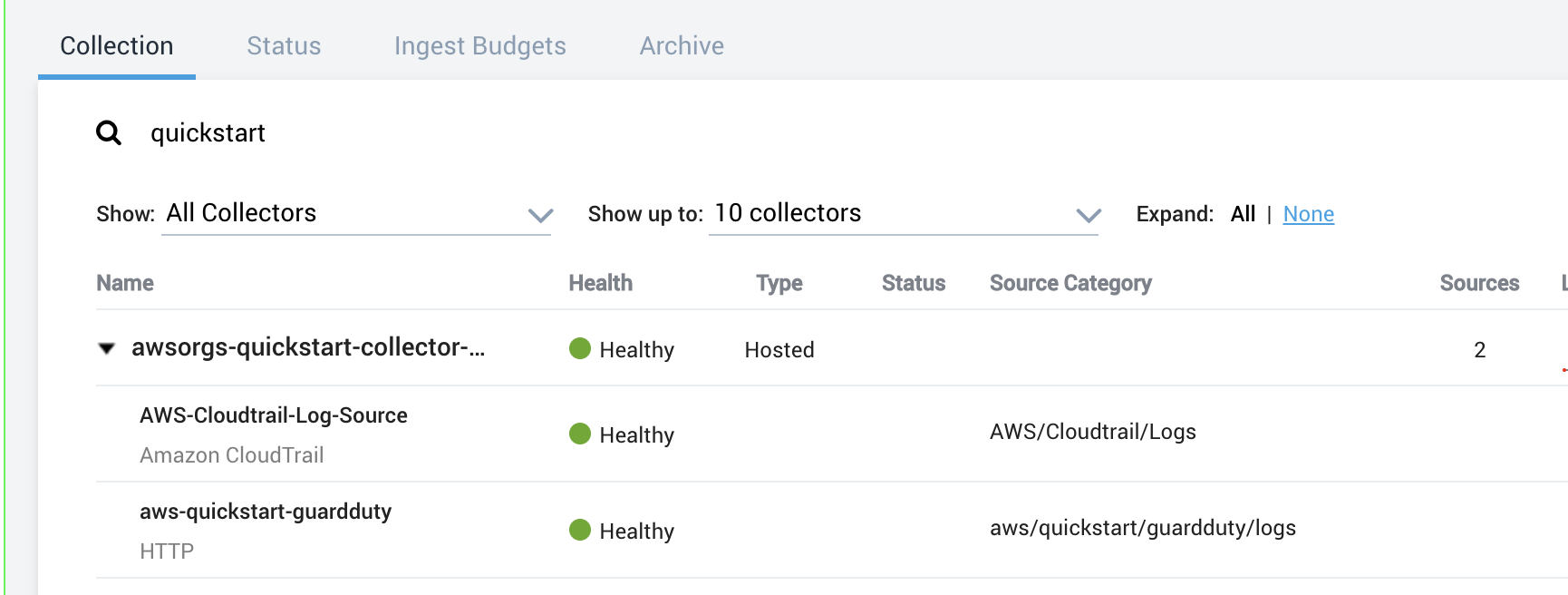
Scenario 1: You do not use AWS security services or Sumo Logic. You did not configure AWS to use AWS security services covered by this Quick Start, but you want to use Sumo Logic apps to collect and analyze data. For this scenario, use this Quick Start to set up AWS security services and configure Sumo Logic. This scenario creates a new Sumo Logic hosted collector called
awsorgs-quickstart-collectorinstalls sources for each app under it. -
Scenario 2: You use AWS security services but not Sumo Logic. You use the AWS security services covered by this Quick Start but have not configured Sumo Logic to collect data from AWS or installed the corresponding Sumo Logic apps. For this scenario, configure the auxiliary AWS services and resources to send data to Sumo Logic. This scenario also installs the corresponding Sumo Logic apps. You can reuse existing sources, and this scenario creates a new Sumo Logic hosted collector called
awsorgs-quickstart-collectorinstalls new sources for each app under it. -
Scenario 3: You use AWS security services and Sumo Logic. You use the AWS security services covered by this Quick Start and you collect and analyze data from one or more of them in Sumo Logic. For this scenario, configure the auxiliary AWS services and resources to send data to Sumo Logic. This scenario is intended only for AWS security services that are not configured and their corresponding Sumo Logic apps. You can reuse existing sources, and this scenario creates a new Sumo Logic hosted collector called
awsorgs-quickstart-collectorinstalls new sources for each app under it.
Predeployment steps
Before deploying this Quick Start, complete the following steps:
-
If you don’t already have a Sumo Logic enterprise account, create one at https://sumologic.com by following the on-screen instructions.
-
If you don’t already have an AWS organization, create one. For more information, refer to Tutorial: Creating and configuring an organization.
-
Ensure that your IAM user has sufficient permissions for the IAM user or role in your organization management account to create an organization trail and enable GuardDuty.
-
Enable trusted access with AWS Organizations. For more information, refer to Enable trusted access with AWS Organizations. Otherwise, since this is a multi-account deployment, AWS CloudFormation won’t run.
-
If you don’t already have them, create separate security tooling and log archive accounts in your AWS organization.
-
Ensure that GuardDuty has not been enabled by the security tooling account (delegated administrator). For more information, refer to Managing GuardDuty accounts with AWS Organizations.
-
Become familiar with the additional resources, later in this guide.
Existing AWS security service configurations
If you’re already sending Elastic Load Balancing (ELB) data to Sumo Logic, the Threat Intel for AWS app can report that data.
If you’ve already configured one or more AWS services listed in Table 1, follow the steps provided for that service in the table. If you have not configured these services, this Quick Start automatically configures them when you install the Sumo Logic apps.
| AWS security service | If you’ve done the following… | … do this now: |
|---|---|---|
AWS CloudTrail |
Configured AWS CloudTrail to send logs to an S3 bucket from member accounts. |
1. Enable your member account to send logs to your organization trails. For more information, refer to Organization CloudTrail. 2. Confirm that your organization trails work. 3. Delete redundant Sumo Logic collector, sources, and app folder. For more information, refer to Security OU – Log Archive account. |
Amazon GuardDuty |
Configured Amazon GuardDuty for individual member accounts with no delegated administrator account. |
1. Ensure that new SumoLogic sources created by the Quick Start ingest GuardDuty events. 2. Delete the redundant Sumo Logic resources, such as collector, sources, and app folder. |
AWS Security Hub |
Configured AWS Security Hub for individual member accounts with no delegated administrator account. |
1. Ensure that new SumoLogic sources created by the Quick Start ingest Security Hub events. 2. Delete the redundant SumoLogic resources, such as collector, sources, and app folder. |
AWS WAF - Web Application Firewall |
Configured AWS WAF to send its logs to Amazon Kinesis Data Firehose from member accounts |
1. Ensure that new SumoLogic sources created by the Quick Start ingest AWS WAF logs. 2. Delete the redundant SumoLogic resources, such as collector, sources, and app folder. |
AWS Network Firewall |
Configured AWS Network Firewall to send its logs to an S3 bucket from member accounts. |
1. Ensure that new SumoLogic sources created by the Quick Start ingest Network Firewall events. 2. Delete the redundant SumoLogic resources, such as collector, sources, and app folder. |
Deployment steps
-
Sign in to your AWS account, and launch this Partner Solution, as described under Deployment options. The AWS CloudFormation console opens with a prepopulated template.
-
Choose the correct AWS Region, and then choose Next.
-
On the Create stack page, keep the default setting for the template URL, and then choose Next.
-
On the Specify stack details page, change the stack name if needed. Review the parameters for the template. Provide values for the parameters that require input. For all other parameters, review the default settings and customize them as necessary. When you finish reviewing and customizing the parameters, choose Next.
Unless you’re customizing the Partner Solution templates or are instructed otherwise in this guide’s Predeployment section, don’t change the default settings for the following parameters: QSS3BucketName,QSS3BucketRegion, andQSS3KeyPrefix. Changing the values of these parameters will modify code references that point to the Amazon Simple Storage Service (Amazon S3) bucket name and key prefix. For more information, refer to the AWS Partner Solutions Contributor’s Guide. -
On the Configure stack options page, you can specify tags (key-value pairs) for resources in your stack and set advanced options. When you finish, choose Next.
-
On the Review page, review and confirm the template settings. Under Capabilities, select all of the check boxes to acknowledge that the template creates AWS Identity and Access Management (IAM) resources that might require the ability to automatically expand macros.
-
Choose Create stack. The stack takes about 60 minutes to deploy.
-
Monitor the stack’s status, and when the status is CREATE_COMPLETE, the Sumo Logic Security Integrations for AWS Organizations deployment is ready.
-
To view the created resources, choose the Outputs tab.
Postdeployment steps
If using an existing S3 bucket
If you use an existing S3 bucket with logs, create an SNS topic (SumoSNSTopic-{StackName}) that subscribes to the Sumo Logic sources. After the deployment completes, add that SNS topic to the S3 bucket events. For more information, refer to Enabling and configuring event notifications using the Amazon S3 console.
View the Sumo Logic dashboards
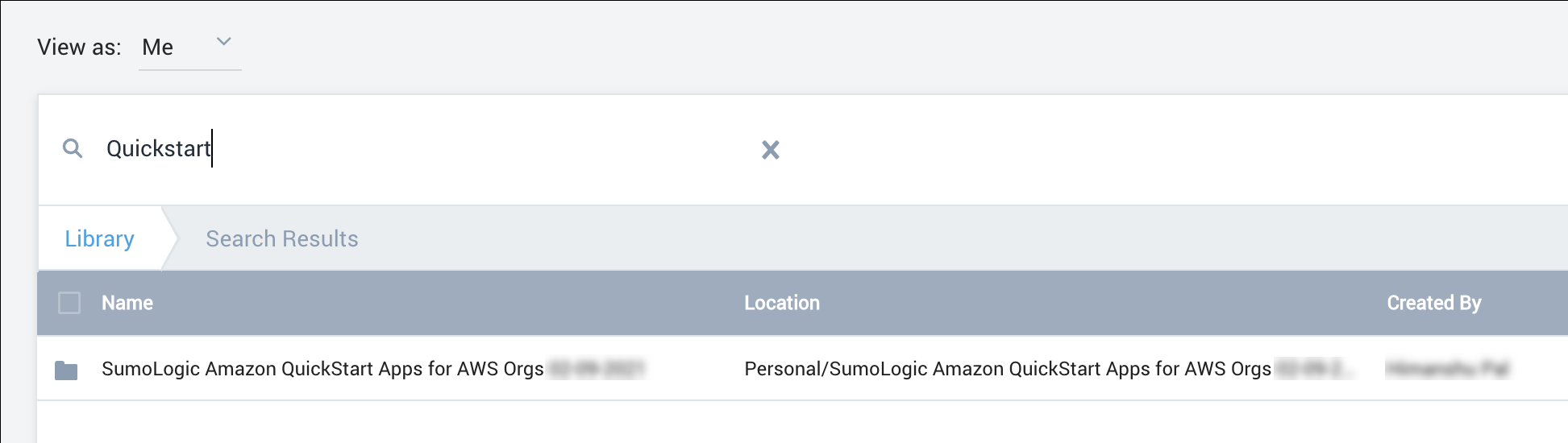
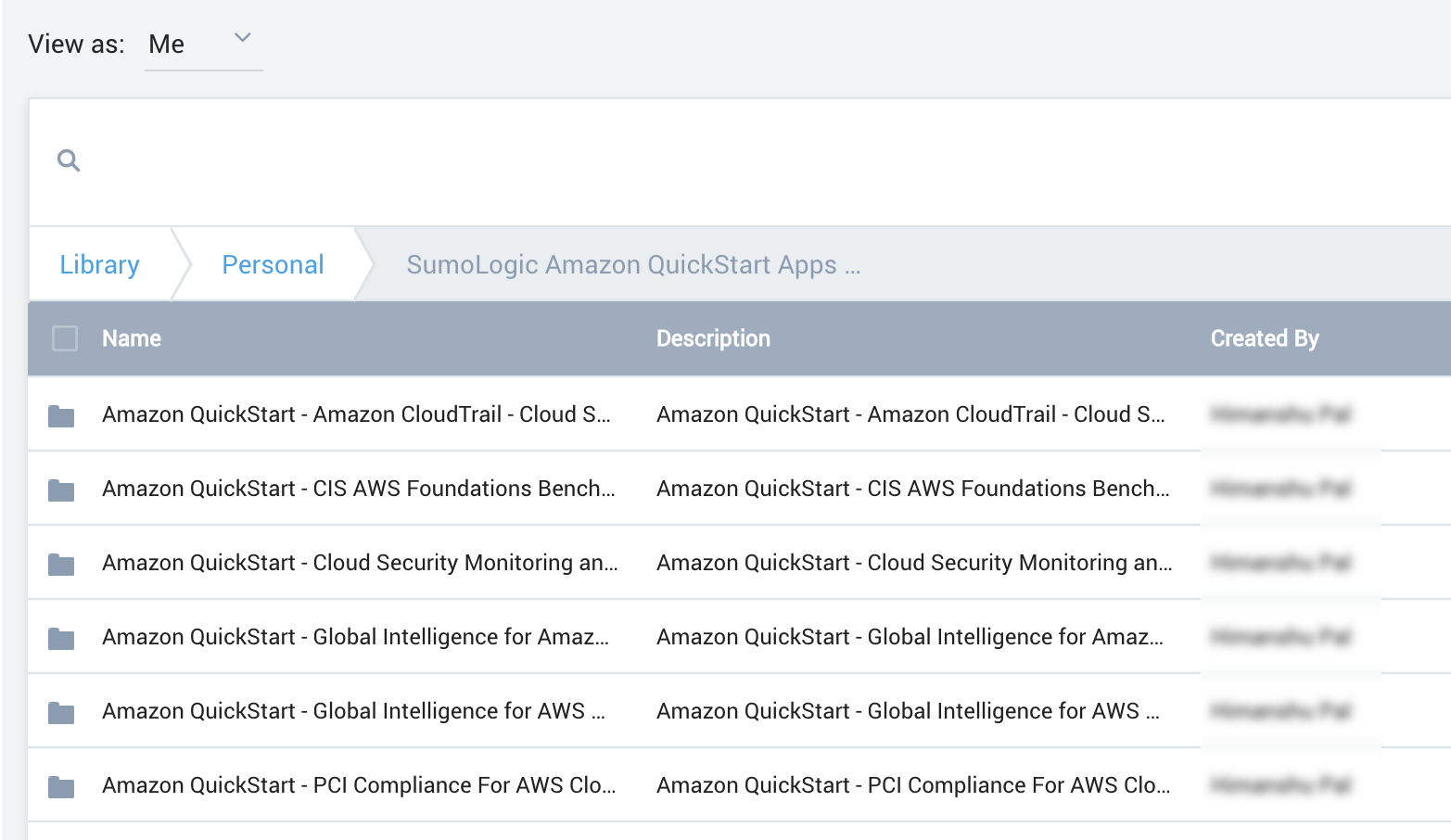
After the deployment completes, the Sumo Logic apps are added to your Sumo Logic personal-account library in a folder named SumoLogic Amazon QuickStart Apps for AWS Orgs <date>, as shown in Figure 2.
Under the SumoLogic Amazon QuickStart Apps <date> folder, there are subfolders that represent each app along with the date and timestamp.
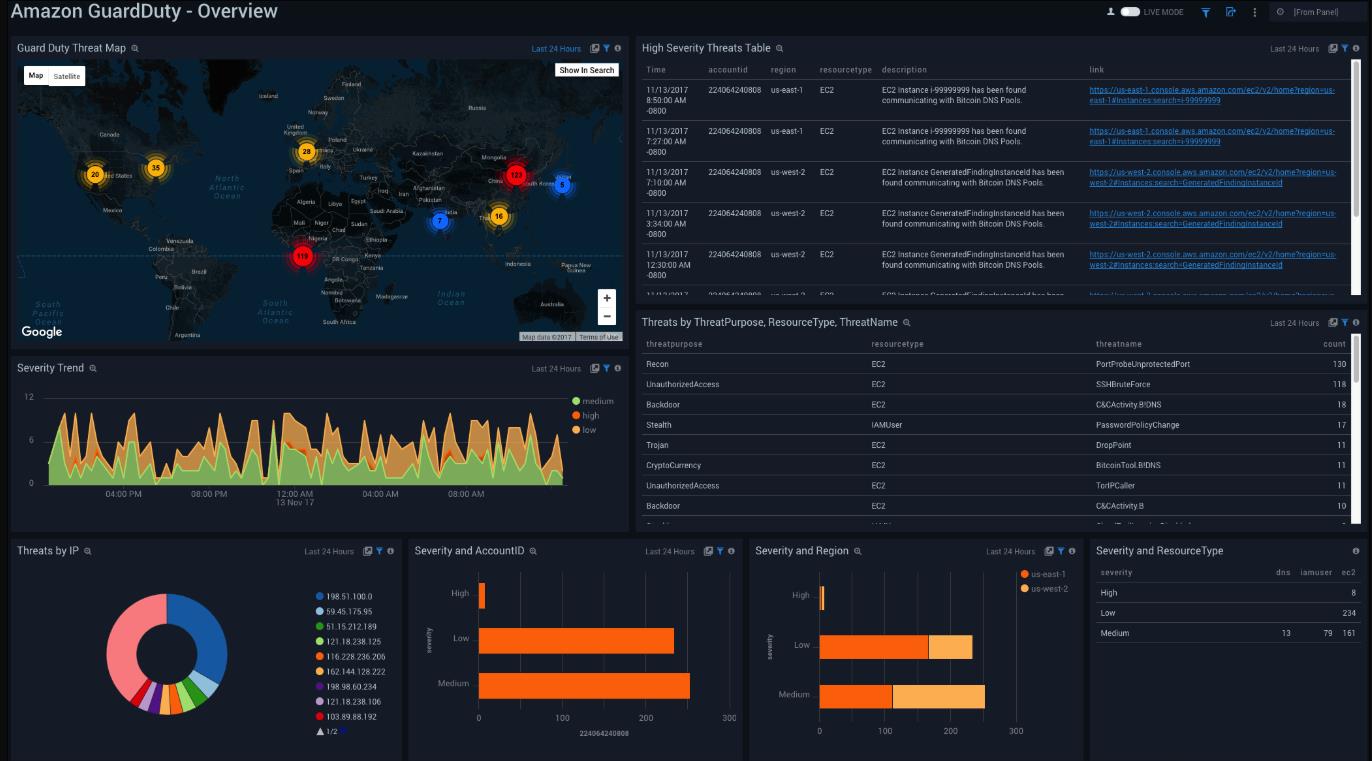
To open the services dashboard, choose its folder in the Sumo Logic console. For instance, under the Amazon GuardDuty folder, open the Amazon GuardDuty – Overview dashboard to see detected threats.
Firewall Manager security group
The deployment creates a security group that is used by Firewall Manager only as a comparison reference for the security groups that are in scope of the policy. Firewall Manager doesn’t associate it with any resources in your organization. You can update the security group for your use case. For more information, refer to Security group policies.
Firewall Manager creates a web ACL in each account that’s managed by Firewall Manager.
AWS Firewall Manager managed Network Firewall policies
Firewall Manager Network Firewall Policies allow Firewall Manager to manage AWS Network Firewall firewalls for your Amazon Virtual Private Cloud VPCs across your organization in AWS Organizations. For each account and VPC that’s within policy scope, Firewall Manager creates a Network Firewall firewall and deploys firewall endpoints to VPC subnets, to filter network traffic.
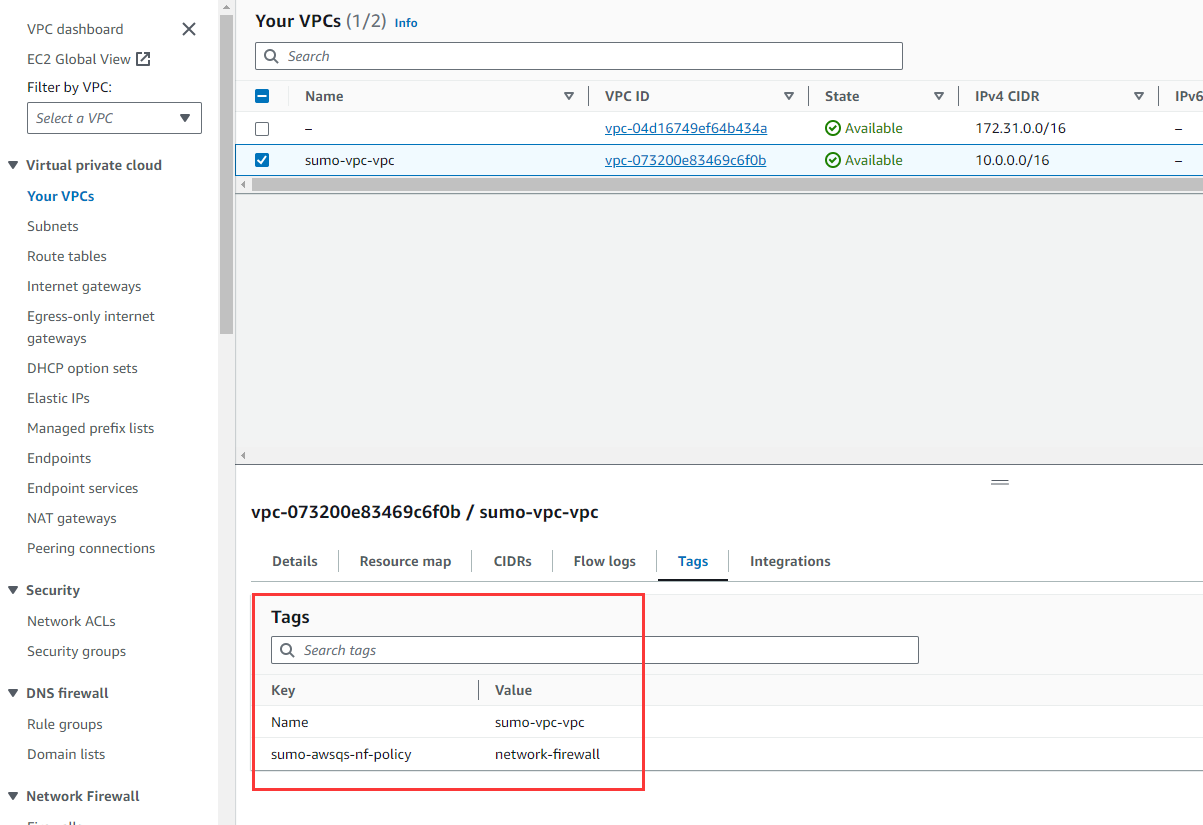
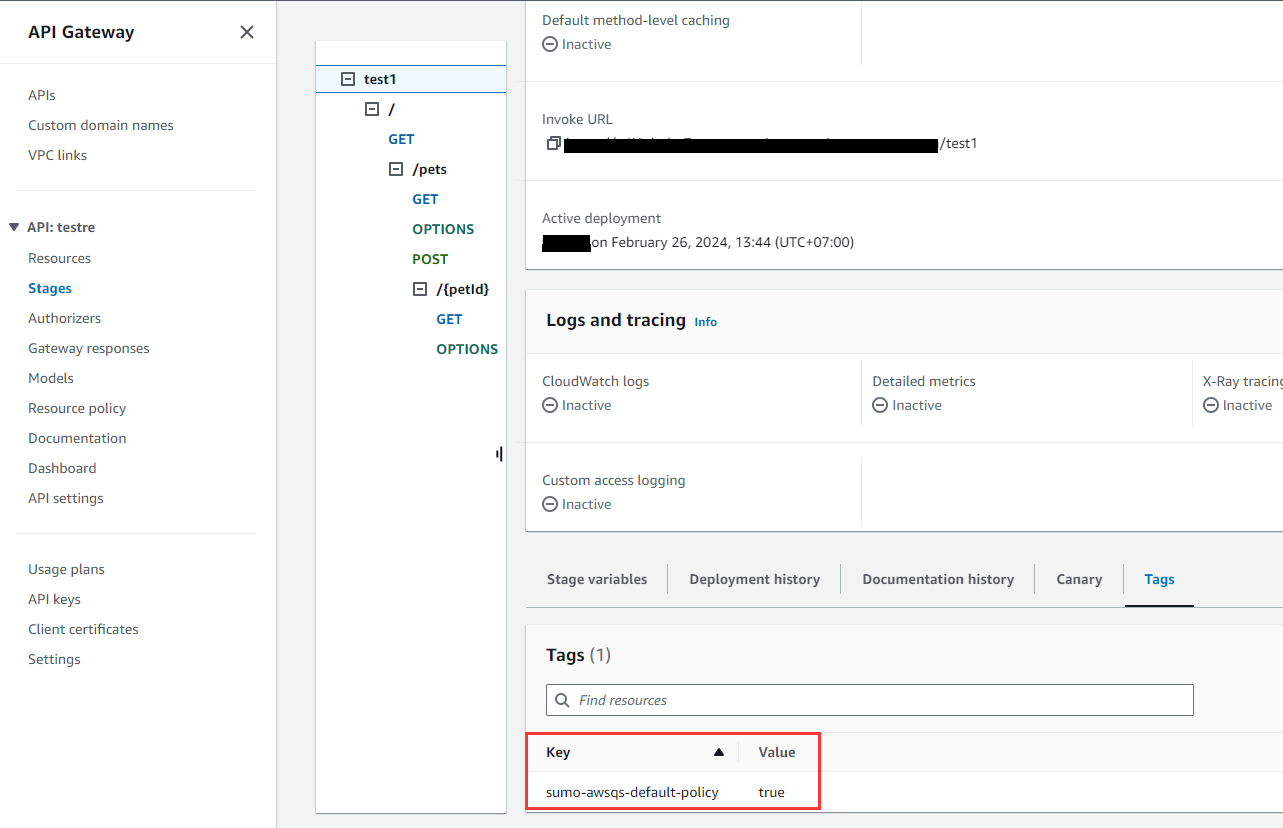
To narrow the scope of your policy, you can tag your VPCs with key: sumo-awsqs-nf-policy and value: network-firewall. For more information about tagging your resources, see Working with Tag Editor.
AWS Firewall Manager managed WAF policies
Firewall Manager WAF Policies allow Firewall Manager to centrally mandate the application of AWS WAF Rule sets and Web ACLs to endpoints (ELBs, CloudFront Distributions, and API Gateway) in the environment.
The solution enforces the policies based on resource tags. For more information about tags, see Working with Tag Editor.
The following WAF Policies list includes the resource tags which needs to be added for supported resource types to enable AWS Managed rule sets:
-
FMS Regional WAF Default Policy
-
Resource Types
-
ELBv2
-
API Gateway
-
-
AWS Managed Rule sets
-
AWS Core Ruleset
-
AWS SQL Database Ruleset
-
AWS IP Reputation List
-
-
Resource Tag
-
Key: sumo-awsqs-default-policy
-
Value: true
-
-
-
FMS CloudFront Default Policy
-
Resource Types
-
Cloudfront Distribution
-
-
AWS Managed Rule sets
-
AWS Core Ruleset
-
AWS SQL Database Ruleset
-
AWS IP Reputation List
-
-
Resource Tag
-
Key: sumo-awsqs-default-policy
-
Value: true
-
-
-
FMS Regional WAF Windows Policy
-
Resource Types
-
ELBv2
-
API Gateway
-
-
AWS Managed Rule sets
-
AWS Windows Operating System Ruleset
-
-
Resource Tag
-
Key: sumo-awsqs-windows-policy
-
Value: windows
-
-
-
FMS Regional WAF Linux Policy
-
Resource Types
-
ELBv2
-
API Gateway
-
-
AWS Managed Rule sets
-
AWS Linux Operating System Ruleset
-
-
Resource Tag
-
Key: sumo-awsqs-linux-policy
-
Value: linux
-
-
-
FMS Regional WAF Posix Policy
-
Resource Types
-
ELBv2
-
API Gateway
-
-
AWS Managed Rule sets
-
AWS Posix Operating System Ruleset
-
-
Resource Tag
-
Key: sumo-awsqs-posix-policy
-
Value: posix
-
-
Kinesis Data Firehose delivery stream
Monitor your delivery stream to ensure that it has enough throughput to accommodate your organization’s WAF logs.
Test the deployment
AWS account
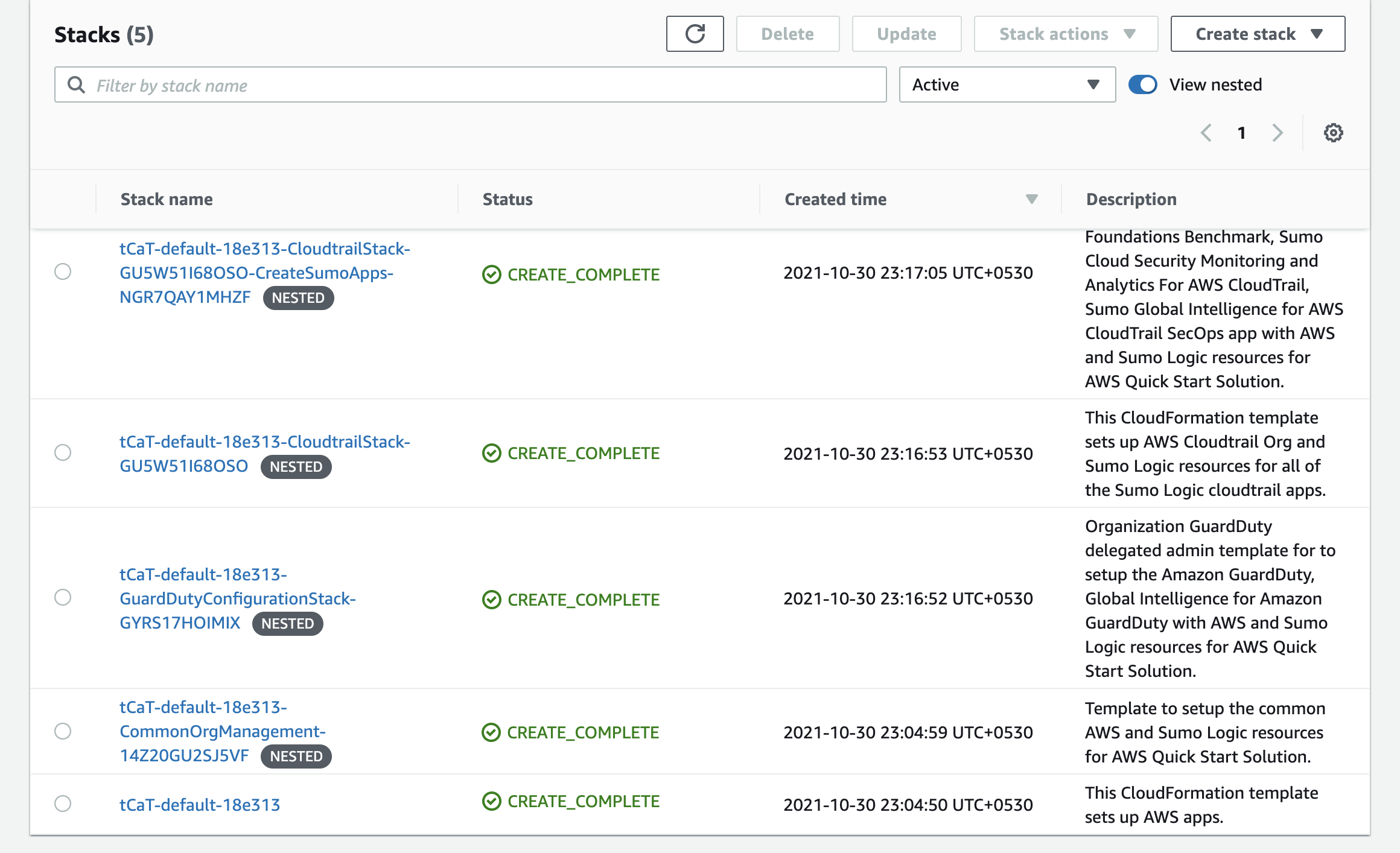
After the deployment completes, you see the main stack, QuickStartApps, in addition to multiple nested stacks.
Additional resources
Sumo Logic documentation
AWS services
Other AWS documentation
Troubleshooting
-
For troubleshooting common Quick Start issues, refer to the AWS Quick Start General Information Guide and Troubleshooting CloudFormation.
-
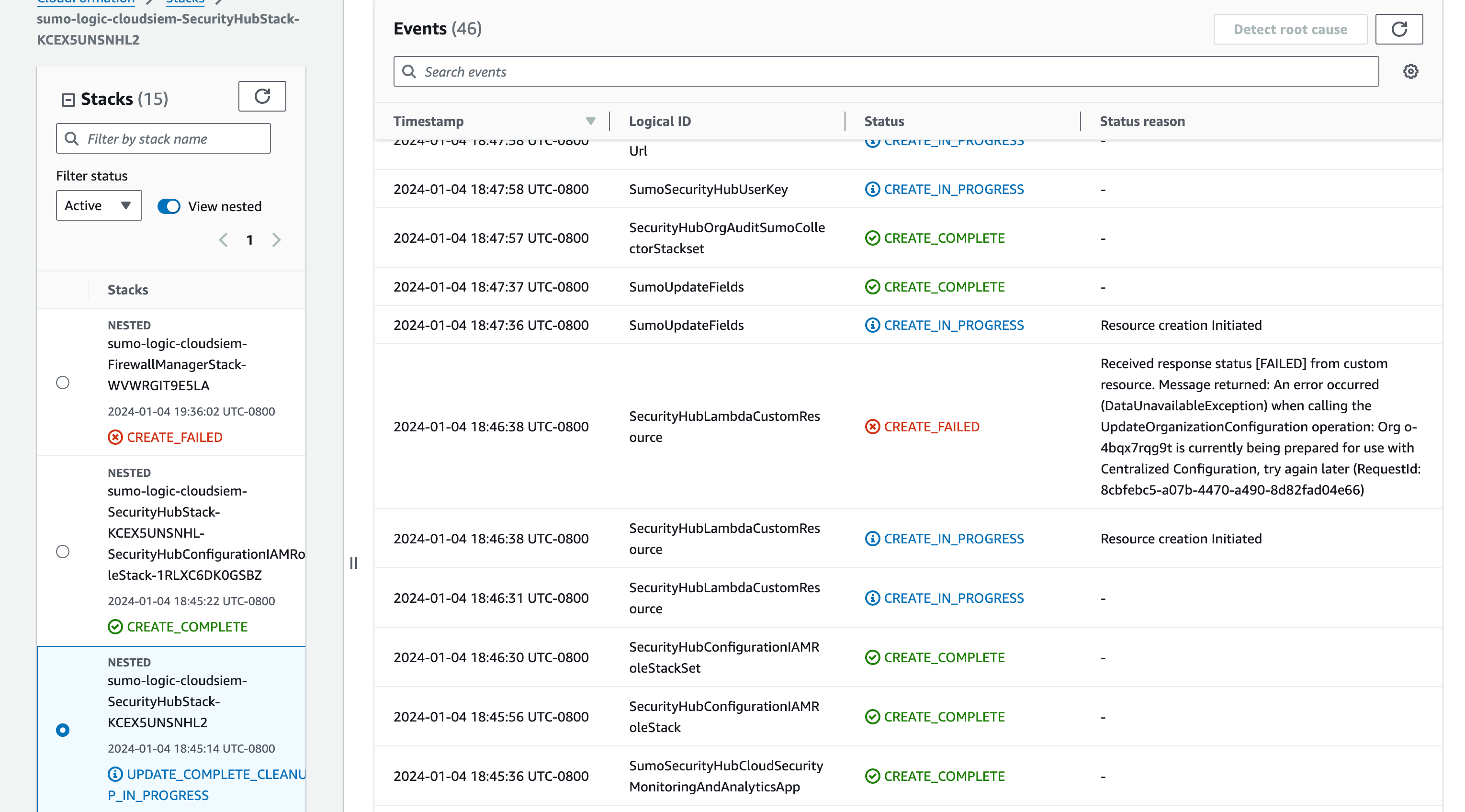
If your AWS Organizations is new, you might run into the below issue for Security Hub Centralized Configuration and you would need to retry the deployment in 24 hours.
Customer responsibility
After you deploy a Partner Solution, confirm that your resources and services are updated and configured—including any required patches—to meet your security and other needs. For more information, refer to the Shared Responsibility Model.
Feedback
To submit feature ideas and report bugs, use the Issues section of the GitHub repository for this Partner Solution. To submit code, refer to the Partner Solution Contributor’s Guide. To submit feedback on this deployment guide, use the following GitHub links:
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS products or services, each of which is provided "as is" without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at https://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "as is" basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.