Sumo Logic Security Integrations on AWS
Partner Solution Deployment Guide

November 2021
Arun Patyal and Himanshu Pal, Sumo Logic
Dilip Rajan and Vinay Maddi, AWS Data & Analytics Partner SA team
Shivansh Singh and Suresh Veeragoni,, AWS Integration & Automation team

| Refer to the GitHub repository to view source files, report bugs, submit feature ideas, and post feedback about this Partner Solution. To comment on the documentation, refer to Feedback. |
This Partner Solution was created by Sumo Logic in collaboration with Amazon Web Services (AWS). Partner Solutions are automated reference deployments that help people deploy popular technologies on AWS according to AWS best practices. If you’re unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Overview
This guide covers the information you need to deploy the Sumo Logic Security Integrations Partner Solution in the AWS Cloud.
This Amazon Web Services (AWS) Partner Solution automatically deploys Sumo Logic Security Integrations on the AWS Cloud. It’s for people who want to configure the Sumo Logic console for 12 AWS services that provide security analytics for a single AWS account. With the default settings, this Partner Solution deploys CloudTrail and GuardDuty apps.
Sumo Logic Security Integrations on AWS
Sumo Logic is focused on continuous intelligence, a category of software that addresses data challenges presented by digital transformations, modern applications, and cloud computing. The Sumo Logic Continuous Intelligence Platform automates the collection, ingestion, and analysis of applications, infrastructure, security, and Internet of Things (IoT) data to derive actionable insights.
This Partner Solution uses Sumo Logic Cloud SIEM (security information and incident management) powered by AWS. Sumo Logic Cloud SIEM uses apps to collect security events generated by AWS and other security services to provide an aggregate view of overall security and compliance posture.
Sumo Logic has apps for each AWS security service (for example, the Sumo Logic app for AWS CloudTrail) and apps that support multiple AWS services (for example, Threat Intel for AWS). Sumo Logic customers can track user activity, monitor threats, and understand how their security posture compares with global benchmarks. Sumo Logic also uses apps to audit and help maintain compliance with the Payment Card Industry (PCI) Data Security Standard (DSS) and Center for Internet Security (CIS).
The included template automatically creates resources that use various AWS services to collect logs, which are sent to your preregistered Sumo Logic account.
| Deploying this solution does not guarantee an organization’s compliance with any laws, certifications, policies, or other regulations. |
Costs and licenses
Sumo Logic provides a free tier with unlimited queries and 30-day free trials for various licensing options. For details on pricing, visit the Sumo Logic website.
There is no cost to use this Partner Solution, but you will be billed for any AWS services or resources that this Partner Solution deploys. For more information, refer to the AWS Partner Solution General Information Guide.
Architecture
Deploying this Partner Solution with default parameters builds the following Sumo Logic environment in the AWS Cloud.
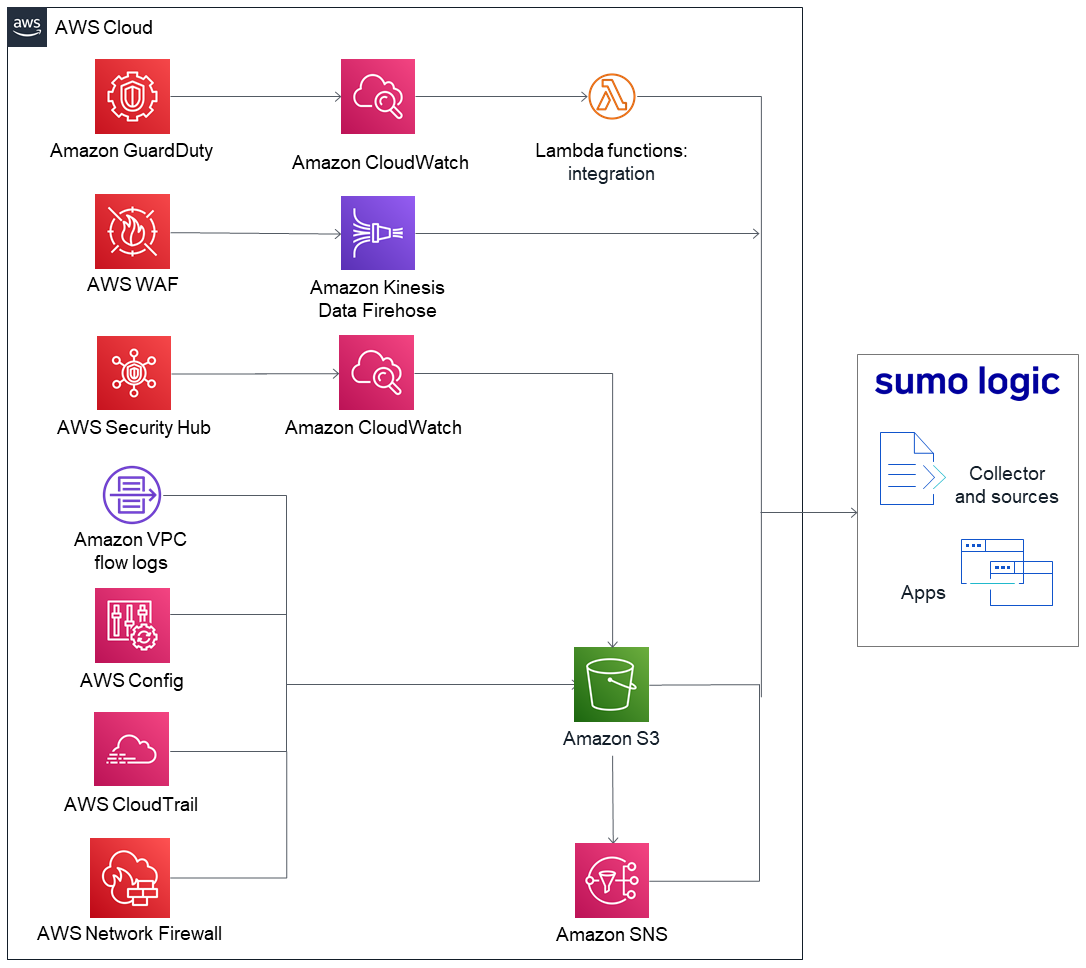
As shown in Figure 1, this Partner Solution sets up the following:
-
Amazon GuardDuty to detect malicious activity and behavior to protect AWS accounts and workloads.
-
Amazon VPC flow logs to capture information about IP traffic going to and from network interfaces in your VPC.
-
Amazon CloudWatch for relaying the Amazon VPC flow logs to the Lambda function.
-
AWS Security Hub to assess security alerts and security posture across AWS accounts. Security Hub relays security events to Amazon CloudWatch.
-
AWS WAF to protect your web applications from common web exploits.
-
AWS Config to record and evaluate configurations of your AWS resources.
-
AWS CloudTrail to track user activity and API (application programming interface) usage.
-
AWS Network Firewall to deploy essential network protections for all your Amazon virtual private clouds (VPCs).
-
Amazon Kinesis Data Firehose delivery streams to transfer logs from AWS WAF to the Amazon S3 bucket.
-
AWS Lambda functions to create a collector and multiple sources and to install apps on your Sumo Logic account.
-
An Amazon S3 bucket to capture logs from the various AWS services.
-
Amazon Simple Notification Service (Amazon SNS), which is invoked when a new object is saved to an S3 bucket.
-
The Sumo Logic collector and sources to receive logs from the S3 bucket.
Deployment options
This Partner Solution provides one deployment option.
-
Deploy Sumo Logic Security Integrations. You build a new AWS environment that consists of the infrastructure resources required to provision applications to your Sumo Logic account and the necessary resources to your AWS account. During the deployment, you can choose which applications to install.
Scenarios supported by this Partner Solution
This Partner Solution supports the following scenarios:
-
Scenario 1: You do not use AWS security services or Sumo Logic. You did not configure AWS to use one or more security services listed under Specialized knowledge, but you want to collect and analyze data using Sumo Logic apps. For this scenario, use this Partner Solution to set up AWS security services and configure Sumo Logic.
-
Scenario 2: You use AWS security services but not Sumo Logic. You use the AWS security services listed under Specialized knowledge but have not configured Sumo Logic to collect data from AWS or installed the corresponding Sumo Logic apps. For this scenario, configure the auxiliary AWS services and resources to send data to Sumo Logic. This scenario also installs the corresponding Sumo Logic apps.
-
Scenario 3: You use AWS security services and Sumo Logic. You use the AWS security services listed under Specialized knowledge and you collect and analyze data from one or more of them in Sumo Logic. For this scenario, configure the auxiliary AWS services and resources to send data to Sumo Logic. This scenario is intended only for nonconfigured AWS security services and their corresponding Sumo Logic apps.
Note: If you want to collect data from AWS S3 bucket managed by Control Tower, use the cfn-ps-sumo-logic-cloudsiem solution
Predeployment steps
Specialized knowledge
Before you deploy this Partner Solution, be familiar with Sumo Logic. If you are new to Sumo Logic, see Getting Started with Sumo Logic.
Also be familiar with the AWS services listed in Table 1, which shows how various AWS security services map to the corresponding apps in Sumo Logic.
AWS security service or feature |
Sumo Logic apps for the following AWS services or features |
What you need before you deploy this Partner Solution
To deploy this Partner Solution, you need the following:
-
A Sumo Logic enterprise account. If you don’t already have one, create one at https://sumologic.com by following the on-screen instructions.
-
The ability to launch AWS CloudFormation templates that create IAM roles.
-
An understanding of how Sumo Logic resources are created for each scenario (as described earlier under Scenarios supported by this Partner Solution).
-
For data collection, scenario 1, a new Sumo Logic Hosted Collector called
aws-quickstart-collectoris created, and sources for each app are installed under it. -
For data collection scenarios 2 and 3, all existing sources can be reused. All new sources are installed under a new Sumo Logic–hosted collector called
aws-quickstart-collector. -
All Sumo Logic apps are installed in a personal folder called
SumoLogic Amazon QuickStart Apps, followed by the date.
-
| The Threat Intel app can report Elastic Load Balancing (ELB) data if you are already sending that data to Sumo Logic. If you’ve already configured AWS security services to send logs to S3 buckets or SNS topics, collect the following information before you launch the Partner Solution. If you did not previously configure these services, this Partner Solution automatically configures these AWS services and resources when you install the Sumo Logic apps. |
| Sumo Logic apps | If you have done the following | Make a note of: |
|---|---|---|
CloudTrail, PCI DSS compliance for AWS CloudTrail, CIS AWS foundations,Amazon CloudTrail - Cloud Security Monitoring and Analytics, Global Intelligence for AWS CloudTrail SecOps App |
Configured AWS CloudTrail to send its logs to an S3 bucket. |
The S3 bucket name. |
Amazon VPC flow logs, PCI DSS compliance for Amazon VPC flow logs, Amazon VPC flow - Cloud Security Monitoring and Analytics |
Configured Amazon VPC flow logs to send to an S3 bucket. |
The S3 bucket name. |
Amazon S3 Audit |
Configured the access logging of S3 buckets. |
The S3 bucket name. |
AWS WAF |
Configured AWS WAF to send a Kinesis Data Firehose delivery stream to an S3 bucket. |
The S3 bucket name. |
AWS Config |
Configured AWS Config to deliver notifications to an SNS topic. |
The SNS topic. |
Threat Intel |
Configured ELB logs to send data to Sumo Logic. |
The ELB source category in Sumo Logic. |
AWS Network Firewall |
Configured Network Firewall firewall and policy. |
Network Firewall policy Amazon Resource Name (ARN). |
AWS Network Firewall |
Have not configured Network Firewall. |
VPC ID, subnet ID. |
Prepare your Sumo Logic account
-
If you don’t already have a Sumo Logic enterprise account, create one at https://sumologic.com by following the on-screen instructions.
-
Create the access key and access ID from your Sumo Logic account. These are passed as parameters when you launch the Partner Solution template.
-
Get the organization ID from your Sumo Logic account in the Administration section under the Account tab. You must pass this ID.
If you want to use the Threat Intel app but have not configured data collection, see Threat Intel for AWS. If you already configured data collection, note the relevant Sumo Logic source category for your data.
Deployment steps
-
Sign in to your AWS account, and launch this Partner Solution, as described under Deployment options. The AWS CloudFormation console opens with a prepopulated template.
-
Choose the correct AWS Region, and then choose Next.
-
On the Create stack page, keep the default setting for the template URL, and then choose Next.
-
On the Specify stack details page, change the stack name if needed. Review the parameters for the template. Provide values for the parameters that require input. For all other parameters, review the default settings and customize them as necessary. When you finish reviewing and customizing the parameters, choose Next.
Unless you’re customizing the Partner Solution templates or are instructed otherwise in this guide’s Predeployment section, don’t change the default settings for the following parameters: QSS3BucketName,QSS3BucketRegion, andQSS3KeyPrefix. Changing the values of these parameters will modify code references that point to the Amazon Simple Storage Service (Amazon S3) bucket name and key prefix. For more information, refer to the AWS Partner Solutions Contributor’s Guide. -
On the Configure stack options page, you can specify tags (key-value pairs) for resources in your stack and set advanced options. When you finish, choose Next.
-
On the Review page, review and confirm the template settings. Under Capabilities, select all of the check boxes to acknowledge that the template creates AWS Identity and Access Management (IAM) resources that might require the ability to automatically expand macros.
-
Choose Create stack. The stack takes about 10 minutes to deploy.
-
Monitor the stack’s status, and when the status is CREATE_COMPLETE, the Sumo Logic Security Integrations deployment is ready.
-
To view the created resources, choose the Outputs tab.
Test the deployment
AWS account
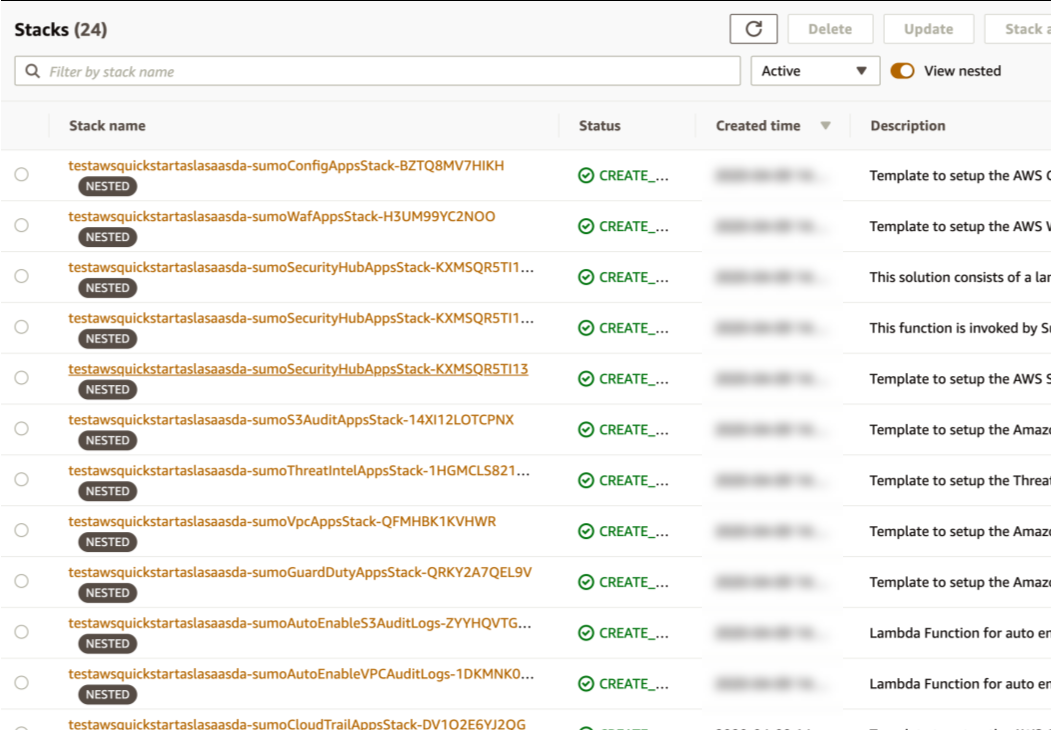
After the deployment completes, you see the main stack, QuickStartApps, in addition to multiple nested stacks.
Sumo Logic account
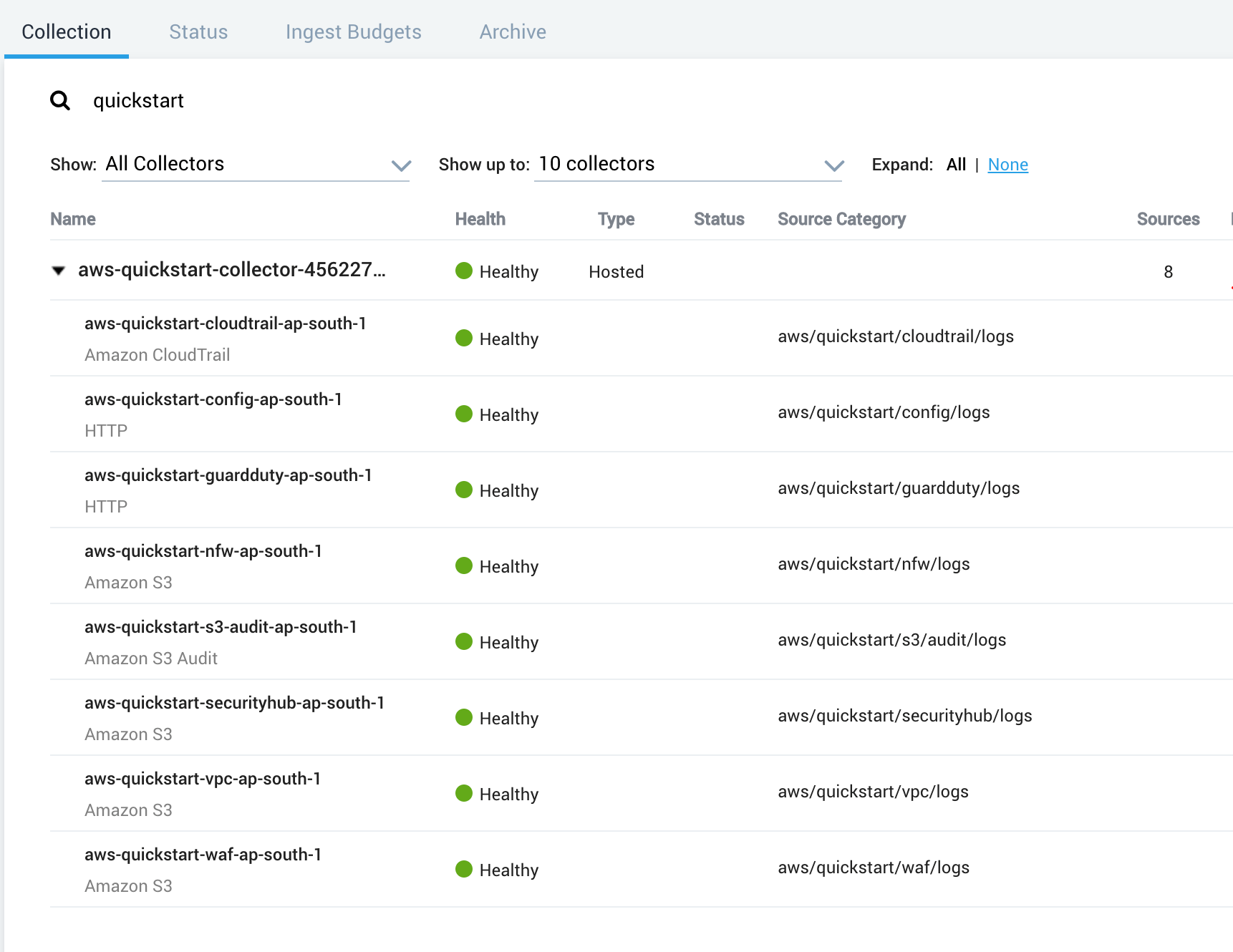
Confirm that the AWS CloudFormation template installed the collectors and sources for your Sumo Logic apps.
Postdeployment steps
If you have not enabled guardduty you need to explicitly enable it
If using a New S3 bucket
You have to configure flow logs in your VPC to export to S3 bucket. You must also enable logging and configure alert and flow logs in your Network Firewall to export to S3 bucket.
If using an existing S3 bucket
If you use an existing S3 bucket with logs, create an SNS topic (SumoSNSTopic-{StackName}) that subscribes to the Sumo Logic sources. After the deployment completes, add that SNS topic to the S3 bucket events. For more information, see How do I enable and configure event notifications for an S3 bucket?
If using AWS WAF logs for an Amazon Kinesis Data Firehose delivery stream
If you install AWS WAF, AWS CloudFormation creates a delivery stream (QuickStartDeliveryStream{Region}) in your Kinesis configuration. You must configure Web ACL in AWS WAF to send logs to the delivery stream. For more information, see Logging Web ACL traffic information.
View the Sumo Logic dashboards
After the deployment completes, the Sumo Logic apps are added to your Sumo Logic personal-account library in a folder named SumoLogic Amazon QuickStart Apps <date>.
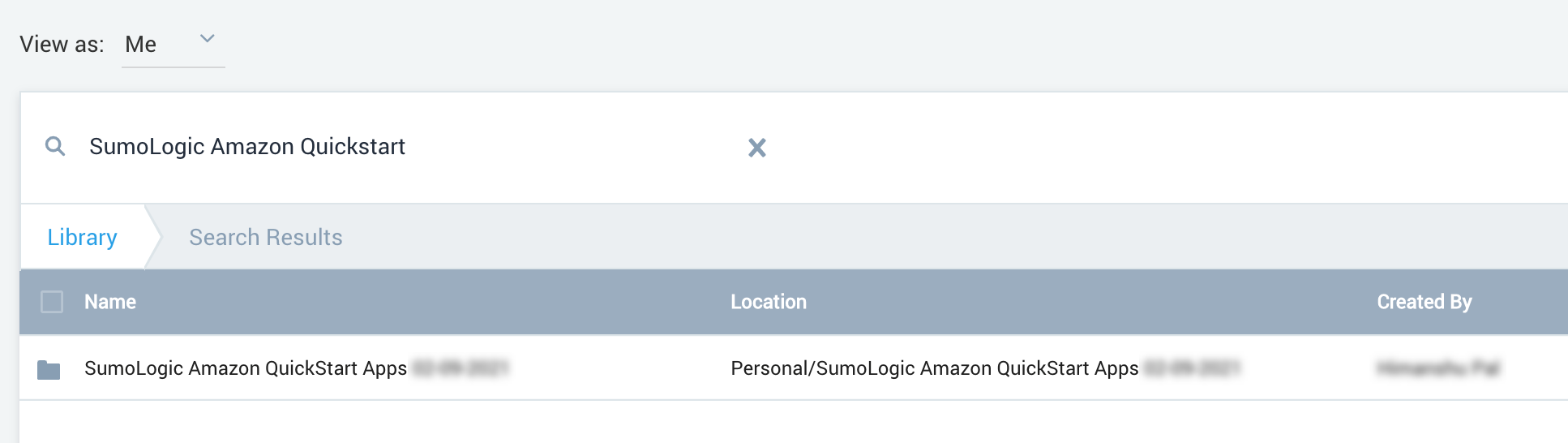
Under the SumoLogic Amazon QuickStart Apps <date> folder, there are subfolders that represent each app along with the date and timestamp.
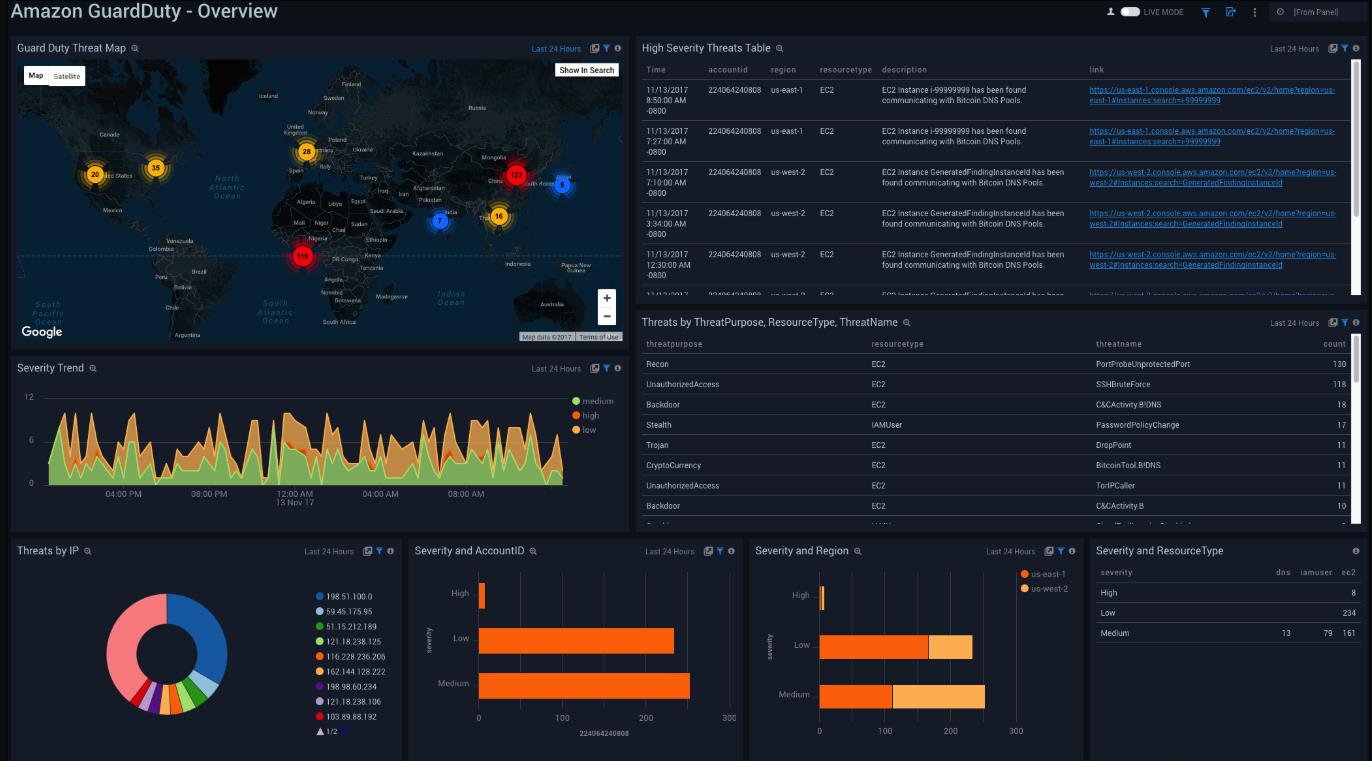
To open the services dashboard, choose its folder in the Sumo Logic console. For instance, under the Amazon GuardDuty folder, open the Amazon GuardDuty – Overview dashboard to see detected threats.
Best practices for using Sumo Logic Security Integrations
If you want to use this Partner Solution across multiple AWS accounts and Regions, rename the top-level parent folder of your Sumo Logic account (under your personal folder) to reflect the correct account and Region.
For each S3 bucket, follow the best practices documented under How can I secure the files in my Amazon S3 bucket? to secure all of your S3 objects. Sumo Logic Security Integrations can monitor the following security and compliance aspects of your AWS environment:
-
Threat monitoring and other security findings
-
Configuration and S3 Audit
-
PCI DSS compliance
-
CIS AWS compliance
Troubleshooting
For troubleshooting common Partner Solution issues, refer to the AWS Partner Solution General Information Guide and Troubleshooting CloudFormation.
Customer responsibility
After you deploy a Partner Solution, confirm that your resources and services are updated and configured—including any required patches—to meet your security and other needs. For more information, refer to the Shared Responsibility Model.
Feedback
To submit feature ideas and report bugs, use the Issues section of the GitHub repository for this Partner Solution. To submit code, refer to the Partner Solution Contributor’s Guide. To submit feedback on this deployment guide, use the following GitHub links:
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS products or services, each of which is provided "as is" without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at https://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "as is" basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.