Amazon VPC Lattice - Simple Client to Server Communication¶
This pattern demonstrates how to expose an EKS cluster hosted application to an internal consumer through Amazon VPC Lattice.
Scenario¶
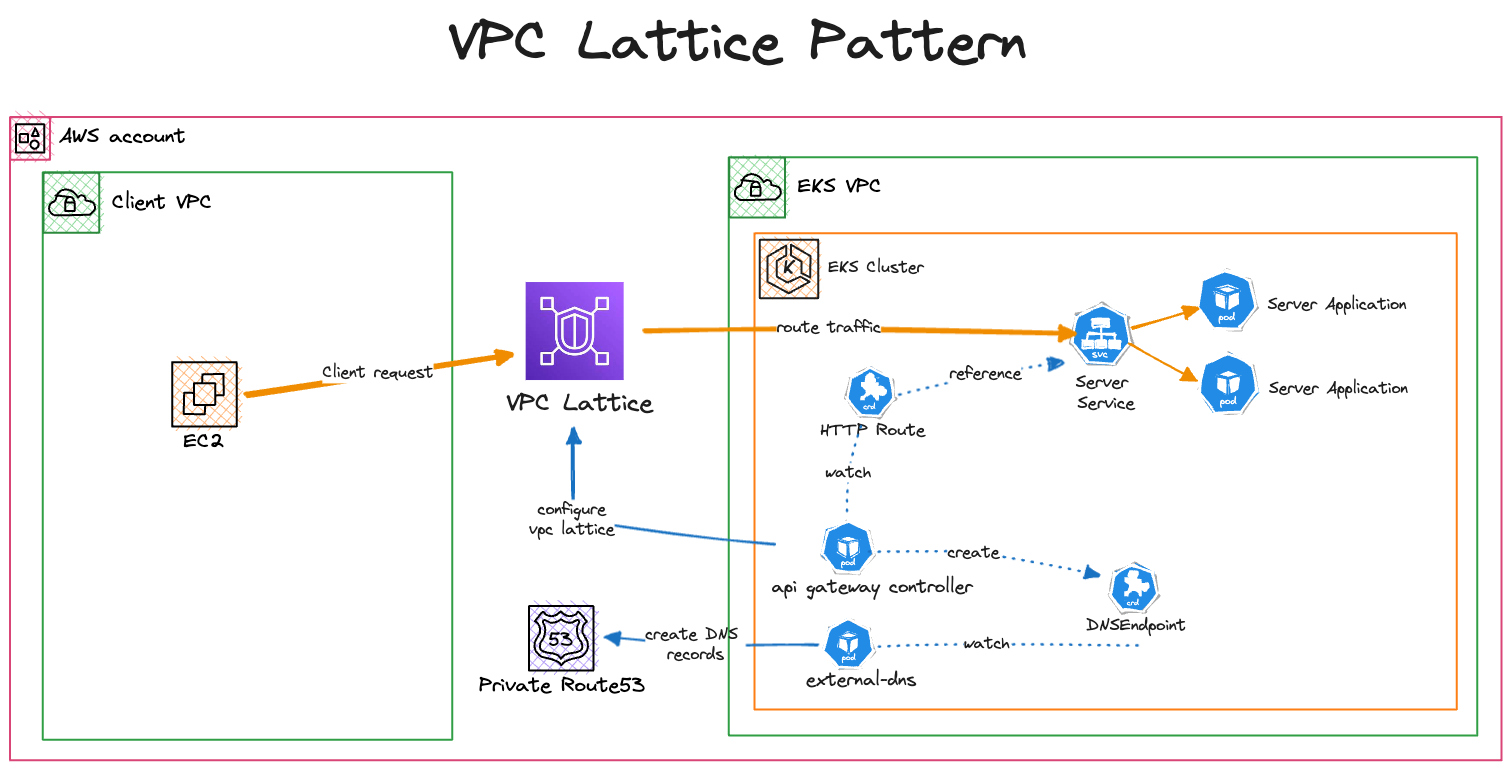
With this solution we showcase how to configure Amazon VPC Lattice using the AWS Gateway API Controller in order to manage Amazon VPC Lattice resources through native K8S Gateway API objects. This pattern deploys two distinct VPCs with a client application running in one of them and a server application in the other. The server application is deployed inside an EKS cluster and made exposed to the client application through Amazon VPC Lattice which establishes connectivity between the two applications. Further we demonstrate how to configure a custom domain name for the exposed service using Amazon Route53 and the external-dns project.
Deploy¶
See here for the prerequisites and steps to deploy this pattern.
Validate¶
In order to test the connectivity between the client and server, please follow the steps outlined below:
- Login to the management console of your AWS account and navigate to the EC2 service
- Select your the EC2 Instance with the name client, click Connect, choose Session Manager and click Connect
-
Within the console test the connectivity to the server application by entering the following command:
Destroy¶
terraform destroy -target="module.eks_blueprints_addons" -auto-approve
terraform destroy -target="module.eks" -auto-approve
terraform destroy -auto-approve
See here for more details on cleaning up the resources created.